Ransomware as a service: Negotiators are now in high demand
RaaS groups are hiring negotiators whose primary role is to force victims to pay up.
By Charlie Osborne for Zero Day | July 8, 2021
The Ransomware-as-a-Service (RaaS) ecosystem is evolving into something akin to a corporate structure, researchers say, with new openings available for "negotiators" -- a role focused on extorting victims to pay a ransom.
On Thursday, KELA threat intelligence analyst Victoria Kivilevich published the results of a study in RaaS trends, saying that one-man-band operations have almost "completely dissolved" due to the lucrative nature of the criminal ransomware business.
The potential financial gains squeezed from companies desperate to unlock their systems have given rise to specialists in cybercrime and extortion and have also led to a high demand for individuals to take over the negotiation part of an attack chain.
Ransomware can be devastating not only to a business's operations but its reputation and its balance sheet. If attackers manage to strike a core service provider used by other businesses, they may also be able to expand their attack surface to other entities quickly.
In a recent case, zero-day vulnerabilities in VSA software provided by Kaseya were used, over the US holiday weekend, to compromise endpoints and put organizations at risk of ransomware infection. At present, it is estimated that up to 1,500 businesses have been affected, at the least due to the need to shut down VSA deployments until a patch is ready.
According to KELA, a typical ransomware attack comprises four stages: malware/code acquisition, spread and the infection of targets, the extraction of data and/or maintaining persistence on impacted systems, and monetization.
There are actors in each 'area,' and recently, demand has increased for extraction and monetization specialists in the ransomware supply chain.
There's a better way to network. Experts are taking notice too. See it in action with a Live Demo:The AI-Driven Enterprise See the real results from our customers. eg. reduce onsite visits by ~90%Time.
Juniper Networks driven by Mist AI delivers the secure AI-Driven Enterprise, focused on optimizing user experiences from client-to-cloud and simplifying IT operations across the WLAN, LAN, WAN, and cloud.
Mist AI revolutionizes traditional networks that are riddled with complexity and technical debt with AI-driven insights and automation for unprecedented scalability, reliability, and agility.
The emergence of so-called negotiators in the monetization arena, in particular, is now a trend in the RaaS space. KELA researchers say that specifically, more threat actors are appearing that manage the negotiation aspect, as well as piling on the pressure -- such as though calls, distributed denial-of-service (DDoS) attacks, and making threats including the leak of information stolen during a ransomware attack unless a victim pays up.
KELA suggests that this role has emerged due to two potential factors: the need for ransomware operators to walk away with a decent profit margin and a need for individuals able to manage conversational English to hold negotiations effectively.
"This part of the attack also seems to be an outsourced activity -- at least for some affiliates and/or developers," Kivilevich says. "The ransomware ecosystem, therefore, more and more resembles a corporation with diversified roles inside the company and multiple outsourcing activities."
Initial access brokers, too, are in demand. After observing dark web and forum activity for over a year, the researchers say that privileged access to compromised networks has surged in price. Some listings are now 25% - 115% more than previously recorded, especially when domain admin-level access has been achieved.
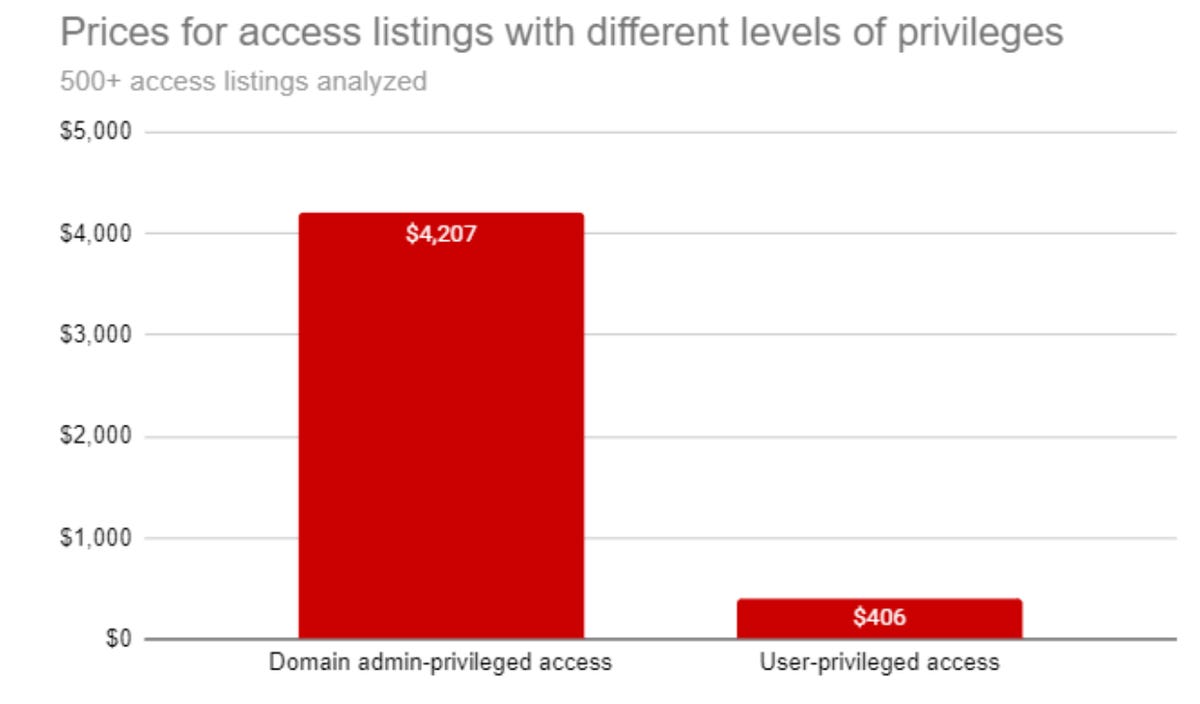
KELA
These intrusion specialists may be paid between 10% and 30% of a ransom payment. However, it should also be noted that some of these brokers will not work with ransomware deployments at all and will only 'sign up' to an attack leveraged against other targets, such as those that will lead to credit card records being obtained.
"During recent years, ransomware gangs grew into cybercrime corporations with members or "employees" specializing in different parts of ransomware attacks and various accompanying services," KELA commented. "The recent ban of ransomware on two major Russian-speaking forums does not seem to affect this ecosystem because only the advertisement of affiliate programs was banned on the forums."
No comments:
Post a Comment