'The regime is bleeding brains': Meet the hackers trying to bring down Belarus' disputed president
By Hannah Somerville • Updated: 14/09/2021

A gathering in Minsk on November 12, 2020 to honour a protester killed during the demonstrations last year. - Copyright AP Photo
The crackdown on dissent in Belarus has been ruthless, methodical and, at times, relentless. Most of Europe had been largely oblivious until the diversion of a Ryanair flight to Minsk and the arrest of a dissident journalist caught people's imagination in May.
But while the authorities may have tried to crush public opposition to long-time president Alexander Lukashenko, they may have only succeeded in driving dissent underground.
Last week, a group of anonymous so-called “ethical hackers” published the latest recording from a massive cache of information seized from the computers of the Belarusian Ministry of Internal Affairs.
In what, if verified, would be one of the most successful hacks of its kind in history, the Belarusian Cyber-Partisans (CP) said in July it had broken into the Ministry’s computers, obtaining more than five terabytes of data.
The group told Euronews that, so far, it had not even published 0.01 per cent of the stolen data. In time, CP says it plans to leak the details of every single operative helping President Alexander Lukashenko crush dissent in the country.
This is the group’s story so far.
The deputy police chief’s premonition
The recorded phone call CP released last Tuesday (September 7) is dated August 17, 2020: about two weeks after nationwide protests erupted over the disputed re-election of Lukashenko, who has ruled Belarus since 1994.
It is understood to have taken place between Podvoisky Igor, deputy police chief for Minsk city, and Kozlov Vitaly, first deputy police chief of Minsk oblast. Given what CP now says it has achieved, it was prescient in more ways than one.
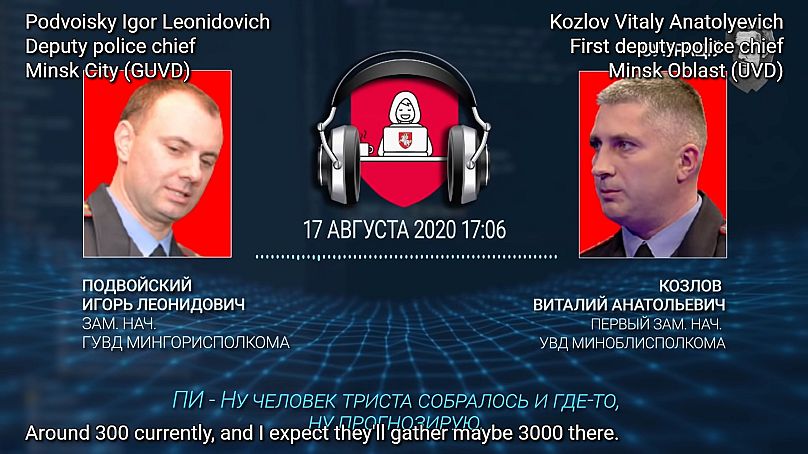
A taped conversation said to be between two Minsk police chiefs in August 2020 was published by CP last week
Belarusian Cyber Partisans
In it, Podvoisky describes his exhaustion after weeks of dealing with what he terms “all this sh*t”. Police, he says, lack a coherent plan of action, state media directors are rebelling, and technical staff are downing tools in droves to join the uprising.
Orders given to police at that time, according to him, were to try to defuse the situation rather than inflame the protests any further. “For now, don’t pressure anyone. Then time will tell… It’s over. There is no plan. Currently, we’re taking the position of protracting the conflict.”
That stance didn’t last. As of March this year more than 33,000 people had been arrested after the regime cracked down on the protests.
The struggle is not over for a democratic Belarus | View
Revolt, repression and reprisals: A look back at a year of turmoil in Belarus
But that day, on August 17, 2020, Lukashenko was apparently in a conciliatory mood. According to the man identified as Podvoisky, he’d waded straight into a crowd of protesters heading for the Ministry of Health and tried to speak in earnest with around 12 of them, one at a time, for about 90 minutes. “[They] didn’t let him insert a word,” the deputy police chief says.
In addition, tellingly, Podvoisky expressed alarm at how the protesters always seemed to know where police and security forces would show up next. When he and others decided internally to leave Minsk Automobile Plant (MAZ) checkpoint via the delivery entrance, they still showed up in their thousands: “In five minutes 2,500 pop up at the gate, with posters.”

In it, Podvoisky describes his exhaustion after weeks of dealing with what he terms “all this sh*t”. Police, he says, lack a coherent plan of action, state media directors are rebelling, and technical staff are downing tools in droves to join the uprising.
Orders given to police at that time, according to him, were to try to defuse the situation rather than inflame the protests any further. “For now, don’t pressure anyone. Then time will tell… It’s over. There is no plan. Currently, we’re taking the position of protracting the conflict.”
That stance didn’t last. As of March this year more than 33,000 people had been arrested after the regime cracked down on the protests.
The struggle is not over for a democratic Belarus | View
Revolt, repression and reprisals: A look back at a year of turmoil in Belarus
But that day, on August 17, 2020, Lukashenko was apparently in a conciliatory mood. According to the man identified as Podvoisky, he’d waded straight into a crowd of protesters heading for the Ministry of Health and tried to speak in earnest with around 12 of them, one at a time, for about 90 minutes. “[They] didn’t let him insert a word,” the deputy police chief says.
In addition, tellingly, Podvoisky expressed alarm at how the protesters always seemed to know where police and security forces would show up next. When he and others decided internally to leave Minsk Automobile Plant (MAZ) checkpoint via the delivery entrance, they still showed up in their thousands: “In five minutes 2,500 pop up at the gate, with posters.”

Thousands-strong crowds protest against Lukashenko's regime in Independence Square, Minsk, on August 23, 2020
AP Photo
“Vitalya,” the man goes on, “I have no f*cking idea how they [the protesters] organised it all. So many details. The preparations must have taken a month or two. It’s incredible, following everybody’s smallest f*cking movement…”
So paranoid was the Belarusian state at that time, it appears that even closed communications between police officers and government officials were being monitored and recorded.
Belarus: 100,000 take to the streets to protest against Lukashenko
Tens of thousands of protesters flood Belarus streets putting pressure on Lukashenko
And 12 months on from those turbulent days, the same issues Podvoisky agonised over on the phone – discontent within the ranks, an exodus of technical staff, and the Belarusian people’s incredible level of self-organisation – would play straight into the hands of groups like CP.
“We never expected to extract so much data undetected,” a representative of the group told Euronews. “But with the current regime, you never know.
“So many high-tech areas are neglected. IT professionals were forced to leave Belarus in the thousands. The regime is bleeding brains they can't make up for.”
Belarus’s digitised revolution
The brains, in this case, belong to a group of around 15 Belarusian citizens and activists, all IT specialists, who joined forces after the protests began last August.
They don’t know each other’s real names. Just three to four are actual hackers, and none are professionals – they learned on the go over the past 12 months.
CP is one member of a bigger consortium of cyberwarriors known as Suprativ, which was formed on September 18, 2020, and includes two other groups, partly made up of ex-regime operatives, called Flying Storks and The People’s Self-Defense Brigade.
The alliance does not recognise Lukashenko as the legitimate ruler of Belarus. Its manifesto lists three goals: “preservation of the independence, sovereignty and territorial integrity of Belarus”, overthrowing the Lukashenko regime, and aiding the country in a stable return to “democratic principles of governance and rule of law”.

“Vitalya,” the man goes on, “I have no f*cking idea how they [the protesters] organised it all. So many details. The preparations must have taken a month or two. It’s incredible, following everybody’s smallest f*cking movement…”
So paranoid was the Belarusian state at that time, it appears that even closed communications between police officers and government officials were being monitored and recorded.
Belarus: 100,000 take to the streets to protest against Lukashenko
Tens of thousands of protesters flood Belarus streets putting pressure on Lukashenko
And 12 months on from those turbulent days, the same issues Podvoisky agonised over on the phone – discontent within the ranks, an exodus of technical staff, and the Belarusian people’s incredible level of self-organisation – would play straight into the hands of groups like CP.
“We never expected to extract so much data undetected,” a representative of the group told Euronews. “But with the current regime, you never know.
“So many high-tech areas are neglected. IT professionals were forced to leave Belarus in the thousands. The regime is bleeding brains they can't make up for.”
Belarus’s digitised revolution
The brains, in this case, belong to a group of around 15 Belarusian citizens and activists, all IT specialists, who joined forces after the protests began last August.
They don’t know each other’s real names. Just three to four are actual hackers, and none are professionals – they learned on the go over the past 12 months.
CP is one member of a bigger consortium of cyberwarriors known as Suprativ, which was formed on September 18, 2020, and includes two other groups, partly made up of ex-regime operatives, called Flying Storks and The People’s Self-Defense Brigade.
The alliance does not recognise Lukashenko as the legitimate ruler of Belarus. Its manifesto lists three goals: “preservation of the independence, sovereignty and territorial integrity of Belarus”, overthrowing the Lukashenko regime, and aiding the country in a stable return to “democratic principles of governance and rule of law”.

The picture CP says is Alexander Lukashenko's passport photo
Belarusian Cyber Partisans
In turn, Suprativ forms part of a vast ecosystem of Belarusian digital activism that fomented for years and was turbo-charged last summer. Protesters used firewall-circumventing software on their phones to get around an internet blackout imposed by Lukashenko on election day, then used social media to organise.
Telegram channels like the Warsaw-based Nexta, founded by 22-year-old dissident blogger Stsiapan Putsila, and Belarus of the Brain kept people informed during those turbulent days by sharing on-the-ground photos and videos of the carnage going on inside the country.
A crowdsourced map of strikes, belzabastovka.org, showed would-be demonstrators where to go, while the Telegram channel Okretsina Lists kept track of those detained.
A constellation of other Belarusian platforms also kept the momentum going. One start-up, PandaDoc, crowdfunded cash to help law enforcement officers pay the heavy fines required to quit their jobs. On September 2, authorities raided its Minsk offices and arrested five staff members.
Meanwhile, campaigns like BY_help and the Belarusian Sport Solidarity Foundation raised funds to support those injured, fined or otherwise targeted during the protests.

In turn, Suprativ forms part of a vast ecosystem of Belarusian digital activism that fomented for years and was turbo-charged last summer. Protesters used firewall-circumventing software on their phones to get around an internet blackout imposed by Lukashenko on election day, then used social media to organise.
Telegram channels like the Warsaw-based Nexta, founded by 22-year-old dissident blogger Stsiapan Putsila, and Belarus of the Brain kept people informed during those turbulent days by sharing on-the-ground photos and videos of the carnage going on inside the country.
A crowdsourced map of strikes, belzabastovka.org, showed would-be demonstrators where to go, while the Telegram channel Okretsina Lists kept track of those detained.
A constellation of other Belarusian platforms also kept the momentum going. One start-up, PandaDoc, crowdfunded cash to help law enforcement officers pay the heavy fines required to quit their jobs. On September 2, authorities raided its Minsk offices and arrested five staff members.
Meanwhile, campaigns like BY_help and the Belarusian Sport Solidarity Foundation raised funds to support those injured, fined or otherwise targeted during the protests.

Nexta and Belarus of the Brain editor-in-chief Roman Protasevich was arrested after his flight to Lithuania was diverted to Minsk earlier this year
AP Photo
Online platform Voice is engaged in a digital re-count of the 2020 election vote and has so far independently verified more than 1.6 million votes in a bid to show the officially-stated outcome was false.
All these initiatives and scores more were entirely self-generated, without state support or financing. The CP activist told Euronews that their own Suprativ alliance was “one big family” – albeit one thrown together by the cruellest of circumstances.
“We were all shocked by what happened in August 2020,” they said. “Each of us individually decided to do something about it.
“We could never have imagined we would grow so much and manage to pull off so many little stabs at the regime (some are not so little). We could never have imagined we would be working hand-in-hand with real-life partisans and have a real shot.”
The MVD hack: Mapping Europe’s last dictatorship
In July and August this year, CP publicly claimed responsibility for a series of cyberattacks on Belarusian state databases and websites. The most important was, it appears, the servers of the Ministry of Internal Affairs (MVD).
The group claims it now has access to the passport details of every single Belarusian citizen, including the files with restricted access such as members of the security services and the Belarusian KGB.

Online platform Voice is engaged in a digital re-count of the 2020 election vote and has so far independently verified more than 1.6 million votes in a bid to show the officially-stated outcome was false.
All these initiatives and scores more were entirely self-generated, without state support or financing. The CP activist told Euronews that their own Suprativ alliance was “one big family” – albeit one thrown together by the cruellest of circumstances.
“We were all shocked by what happened in August 2020,” they said. “Each of us individually decided to do something about it.
“We could never have imagined we would grow so much and manage to pull off so many little stabs at the regime (some are not so little). We could never have imagined we would be working hand-in-hand with real-life partisans and have a real shot.”
The MVD hack: Mapping Europe’s last dictatorship
In July and August this year, CP publicly claimed responsibility for a series of cyberattacks on Belarusian state databases and websites. The most important was, it appears, the servers of the Ministry of Internal Affairs (MVD).
The group claims it now has access to the passport details of every single Belarusian citizen, including the files with restricted access such as members of the security services and the Belarusian KGB.

The group has already released the details of regime officials, including the locations of their villas
Belarusian Cyber Partisans
“We think that the KGB is, for the most part, a repressive and terroristic organisation that contributes very little to the country's security,” the spokesperson said.
“We'll gradually leak all their operatives and plan to assist in building new intelligence agencies in a new Belarus that will actually protect its citizens.”
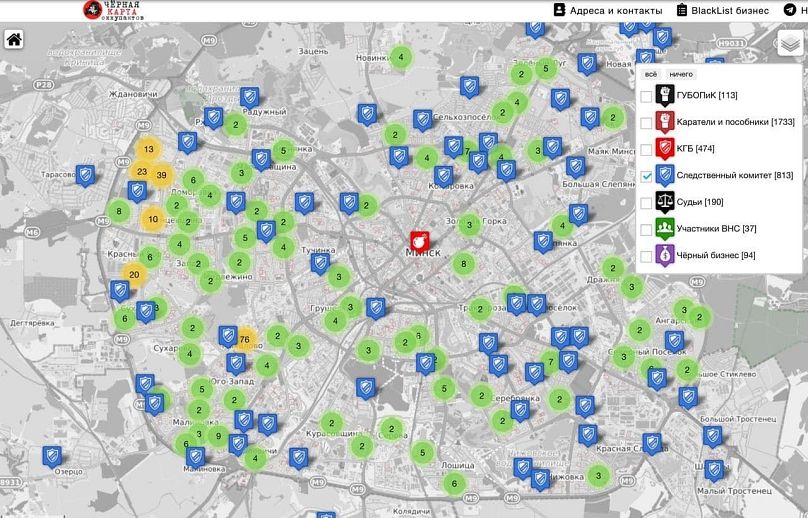
Hundreds of alleged agents’ names and photographs have already been published, as have those of 200 judges. Operatives’ housing assignments were also included in the data.
On June 25 CP published a map detailing the given addresses of 500 state employees, from the secretary of the Republican Youth Union to Investigative Committee members.
“We think that the KGB is, for the most part, a repressive and terroristic organisation that contributes very little to the country's security,” the spokesperson said.
“We'll gradually leak all their operatives and plan to assist in building new intelligence agencies in a new Belarus that will actually protect its citizens.”
Hundreds of alleged agents’ names and photographs have already been published, as have those of 200 judges. Operatives’ housing assignments were also included in the data.
On June 25 CP published a map detailing the given addresses of 500 state employees, from the secretary of the Republican Youth Union to Investigative Committee members.

A map published by CP in September purports to show the Minsk addresses of 500 Belarusian officials
Belarusian Cyber Partisans
The map came together with a statement: “Don’t think that if you didn’t personally beat with a club and didn’t torture people in the gyms of the police department or the temporary detention centre, that you’re removed.
“Those who are now sitting in ironed shirts in cool offices may well be punished for criminal inaction.”
CP has pledged not to touch the data of the millions of ordinary Belarusians whose details were included in the treasure trove. That information is reportedly being kept in encrypted form on a server isolated from the net.
Previously in May, in retaliation for Belarus’s arrest of ex-Nexta chief editor Roman Protasevich after his passenger plane was diverted to Minsk, Suprativ hacked the internal network of the Presidential Academy of Public Administration.
The group deleted academy documents, databases and servers. “Now they will have to work for a long time in the old-fashioned way,” they wrote, “with calculators and pieces of paper.”
The map came together with a statement: “Don’t think that if you didn’t personally beat with a club and didn’t torture people in the gyms of the police department or the temporary detention centre, that you’re removed.
“Those who are now sitting in ironed shirts in cool offices may well be punished for criminal inaction.”
CP has pledged not to touch the data of the millions of ordinary Belarusians whose details were included in the treasure trove. That information is reportedly being kept in encrypted form on a server isolated from the net.
Previously in May, in retaliation for Belarus’s arrest of ex-Nexta chief editor Roman Protasevich after his passenger plane was diverted to Minsk, Suprativ hacked the internal network of the Presidential Academy of Public Administration.
The group deleted academy documents, databases and servers. “Now they will have to work for a long time in the old-fashioned way,” they wrote, “with calculators and pieces of paper.”

Some of the emergency call records CP says it obtained, including calls placed by Belarusian citizens informing on their neighbours
Belarusian Cyber Partisans
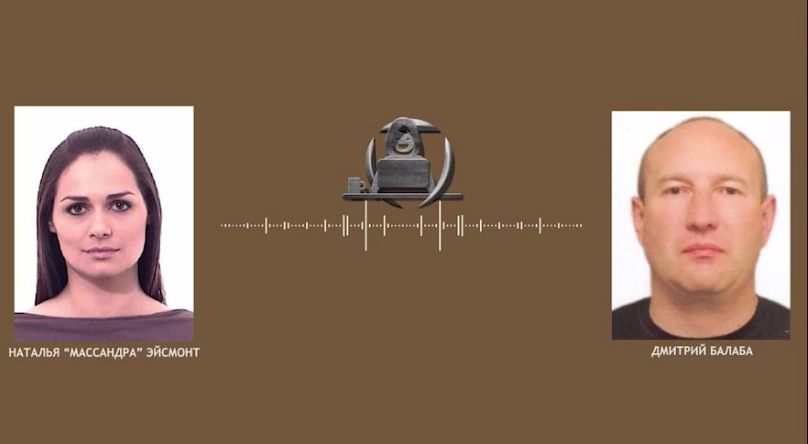
The group also obtained some 10 years’ worth of emergency calls, 16,000 secret internal files including several on Lukashenko and his family – it claimed last month to have published the president’s phone number – and hundreds of thousands of hours of wiretapped phone calls.
“The most revelatory data we obtained are the phone call recordings of the MVD’s internal telephone system,” the CP spokesperson said. “Apparently the regime was recording its own people.
“High-ranking officials felt safe discussing the illegal commands they issued during the crackdown on protests in 2020. The regime kept a lot of incriminating material on its own people intentionally, to be able to extort them in the future and make them commit even harsher crimes.
“We ‘crashed the party’ and ruined their plans. We think this will reduce the chance of violence from the police in the future.”
Other recorded phone calls so far published include a police officer laughing as he describes pulling a woman from her car by the hair and beating her with two SWAT team members, and the head of the ministry saying officials were instructed not to feed or give bed linen to the detainees.
CP was instructed by BYPOL, a group of ex-Belarusian police officers and other defectors, on how to infiltrate some of the computer systems. It says it has hacked the police database and accessed cameras at police stations and jails but has yet to release any footage.

The group also obtained some 10 years’ worth of emergency calls, 16,000 secret internal files including several on Lukashenko and his family – it claimed last month to have published the president’s phone number – and hundreds of thousands of hours of wiretapped phone calls.
“The most revelatory data we obtained are the phone call recordings of the MVD’s internal telephone system,” the CP spokesperson said. “Apparently the regime was recording its own people.
“High-ranking officials felt safe discussing the illegal commands they issued during the crackdown on protests in 2020. The regime kept a lot of incriminating material on its own people intentionally, to be able to extort them in the future and make them commit even harsher crimes.
“We ‘crashed the party’ and ruined their plans. We think this will reduce the chance of violence from the police in the future.”
Other recorded phone calls so far published include a police officer laughing as he describes pulling a woman from her car by the hair and beating her with two SWAT team members, and the head of the ministry saying officials were instructed not to feed or give bed linen to the detainees.
CP was instructed by BYPOL, a group of ex-Belarusian police officers and other defectors, on how to infiltrate some of the computer systems. It says it has hacked the police database and accessed cameras at police stations and jails but has yet to release any footage.

Stills from CCTV footage CP said it had accessed from the Belarusian police database
Belarusian Cyber Partisans
One dismal revelation the group recently reported on Telegram was that COVID-19 deaths in Belarus are likely to have been drastically under-reported to the World Health Organization.
The country’s national statistics portal, Belstat, stopped publishing new mortality data in June 2020. But CP’s passport system hack included the personal data of 1.4 million Belarusians who had died from January 2010 to March 2021.
Independent analysis by the TV channel Current Time found that excess deaths – the number of recorded deaths more than what would be expected in a normal year – from March 2020 to March 2021 stood at 32,000. The country’s officially reported COVID-19 death toll in March was 2,247.
'We removed the masks'
The Belarusian regime has tacitly acknowledged the magnitude of the hack on several occasions in the last month and a half.
At a meeting of the Council of Ministers on August 17, according to the official tribune of the Presidential Administration, Lukashenko warned officials: “If you cannot, as I often say, protect information on your computers, then go back to paper media. Write by hand and put it in your box.”
The head of the KGB, Ivan Tertel, had previously issued a stark warning about foreign hackers during a meeting with local council heads on July 30. “With the use of modern information technologies [and] hacker attacks on personal data,” he said, “a systematic collection of information is carried out.”
One dismal revelation the group recently reported on Telegram was that COVID-19 deaths in Belarus are likely to have been drastically under-reported to the World Health Organization.
The country’s national statistics portal, Belstat, stopped publishing new mortality data in June 2020. But CP’s passport system hack included the personal data of 1.4 million Belarusians who had died from January 2010 to March 2021.
Independent analysis by the TV channel Current Time found that excess deaths – the number of recorded deaths more than what would be expected in a normal year – from March 2020 to March 2021 stood at 32,000. The country’s officially reported COVID-19 death toll in March was 2,247.
'We removed the masks'
The Belarusian regime has tacitly acknowledged the magnitude of the hack on several occasions in the last month and a half.
At a meeting of the Council of Ministers on August 17, according to the official tribune of the Presidential Administration, Lukashenko warned officials: “If you cannot, as I often say, protect information on your computers, then go back to paper media. Write by hand and put it in your box.”
The head of the KGB, Ivan Tertel, had previously issued a stark warning about foreign hackers during a meeting with local council heads on July 30. “With the use of modern information technologies [and] hacker attacks on personal data,” he said, “a systematic collection of information is carried out.”

Lukashenko's spokeswoman Natallia Mikalaeuna Eismant, left, is among those whose calls were apparently recorded by the regime
Belarusian Cyber Partisans
The day after Lukashenko’s comments, a court in Belarus then designated two Telegram accounts linked to CP and Suprativ as ‘extremist’, accusing them of "discrediting law enforcement officers and representatives of government bodies" and "inciting social enmity."
The CP spokesperson alleged the regime was “actively trying” to gather information on the group. “We are very aware of the regime's efforts to infiltrate our rows,” they said. “We have already developed a methodology of working and recruiting new people without compromising the organisation.
“All members are protected by anonymity from other members. The amount of damage any member can cause is limited to the specific project they're working on, at worst. Each member goes through a long process of vetting and demonstrating actual work being done before they get any responsibility.”

The day after Lukashenko’s comments, a court in Belarus then designated two Telegram accounts linked to CP and Suprativ as ‘extremist’, accusing them of "discrediting law enforcement officers and representatives of government bodies" and "inciting social enmity."
The CP spokesperson alleged the regime was “actively trying” to gather information on the group. “We are very aware of the regime's efforts to infiltrate our rows,” they said. “We have already developed a methodology of working and recruiting new people without compromising the organisation.
“All members are protected by anonymity from other members. The amount of damage any member can cause is limited to the specific project they're working on, at worst. Each member goes through a long process of vetting and demonstrating actual work being done before they get any responsibility.”

Supporters of the hacker consortium in Serebryanka, Minsk
Belarusian Cyber Partisans
Apart from sorting the mass of data already acquired, the group says it is working on “other projects” it can’t yet talk about to preserve source security.
The personal information revealed as a result of the hack is arguably a violation of the subjects’ human right to privacy. In Belarus, unauthorised access of computer information is a crime punishable by up to two years in prison; the use of malware carries up to 10.
The CP spokesperson was clear on the group’s rationale. “We see ourselves as leaders of the resistance approach, which acknowledges that all democratic and peaceful ways of regime change have been exhausted in Belarus.
“Lukashenko hasn't left any options for the Belarusian people other than a revolt against the tyranny. We removed the masks of the regime's people that committed crimes.”
Apart from sorting the mass of data already acquired, the group says it is working on “other projects” it can’t yet talk about to preserve source security.
The personal information revealed as a result of the hack is arguably a violation of the subjects’ human right to privacy. In Belarus, unauthorised access of computer information is a crime punishable by up to two years in prison; the use of malware carries up to 10.
The CP spokesperson was clear on the group’s rationale. “We see ourselves as leaders of the resistance approach, which acknowledges that all democratic and peaceful ways of regime change have been exhausted in Belarus.
“Lukashenko hasn't left any options for the Belarusian people other than a revolt against the tyranny. We removed the masks of the regime's people that committed crimes.”
No comments:
Post a Comment