
Dania Akkad
28 July 2022
Legal action in the UK reveals the emotional burden that digital surveillance tools such as Pegasus have had on their targets
We arrive at the location where Ghanem al-Masarir told us to go. But there is no sign of him. A tree-lined trail leading into dark woods? Yes. A field of green grass? Yes. Ghanem? No.
When we agreed to meet at the edge of this country park, on the outskirts of north-west London, it was an unusual plan - but for al-Masarir it made sense.
Back in 2018, the 42-year-old, living in the UK for the past 19 years, was at the peak of his self-made career. That month The Ghanem Show, his YouTube channel which pointedly - and at times wackily - criticised the Saudi royal family hit 300m viewers.
One of al-Masarir's nicknames for Crown Prince Mohammed Bin Salman - the kingdom’s de facto ruler - was Al-dub Al-dasher, the Arabic for stray, fat bear. It had been picked up on social media across the Arab world and even written about in The Economist.
In one episode about the Saudi king and his son he joked: “Now, in the age of Salmanco and his stray bear, also known as double underpants, someone will spend years and years in jail for a tweet.”
Then early one Friday evening that August, while walking in the upscale Knightsbridge neighbourhood of London, al-Masarir was jumped by two men across the street from Harrods. A third man filmed the incident: footage of the attack soon appeared on social media accounts linked to the Saudi government. Al-Masarir was sure the incident was ordered by the crown prince.
Three months later, and within weeks of journalist Jamal Khashoggi’s murder in the Saudi consulate in Istanbul, the Metropolitan Police came to al-Masarir’s London home. There was a credible threat to his life, they told him. A panic button was quickly installed.

Ghanem al-Masarir: "It has affected me in my work life, my personal life, everything, that hacking" (MEE)
Amid all this, Al-Masarir noticed something odd about his iPhones. Their batteries were dying quickly. They refused to update with the latest software. Puzzled, Al-Masarir contacted Citizen Lab, a group of academics at the University of Toronto who focus on communication technology, human rights and global security. It conducted a forensic investigation and discovered that the phones had been hacked with Pegasus, the spyware made by the Israeli company NSO Group that turns phones into military-grade surveillance devices.
Al-Masarir’s movements, his conversations, his photos and his messages, investigators found, had all been fed back to a Saudi server.
It’s now four years later. A cameraman and I are meeting with al-Masarir at a dot he’s marked on a map in this country park. These days, he tells me over an encrypted app, it’s better not to film at his house. I’ve watched clips of his show and an interview he gave to Channel 4 in January 2020, when he’s so chatty that the presenter is forced to cut him off. I’m half expecting Ghanem to jump out of a bush. Or climb out of the white van idling nearby.
But where is he?
Then a figure walks straight towards me. He introduces himself: it’s only then I realise that the man, wrapped in a thick scarf and heavy suede jacket on this hot June day, is the host of The Ghanem Show - or, at least, he was. Al-Masarir tells me, after we find a gnarly log to sit on, that he stopped filming after the events of 2018. “I couldn’t do my show, I couldn’t do anything,” he explains, carefully eyeballing in turn a dog walker, a family and two men passing by.
There had been earlier attempts to silence him. YouTube, says al-Masarir, shut down his channel twice at the request of the Saudi Broadcasting Agency. He had received death threats and threatening phone calls.
Under police protection, and scared to travel anywhere in central London, al-Masarir's life closed in on him. “It has affected me in my work life, my personal life, everything, that hacking," he says. "It has destroyed my appetite to do anything to be honest."
Pegasus in the UK
During the past year, story after story has emerged from nearly every continent of activists, journalists, politicians and others who have been the alleged targets of state-sponsored spyware attacks. Most relate to Pegasus and the leak of list containing more than 50,000 phone numbers. They include Middle East Eye staff.
But the sheer scale of the Pegasus Papers - which were just one leak, about one type of spyware - doesn’t begin to capture the impact that hacking has on the lives of its targets.
Among these are Arab dissidents who for decades have moved to the UK to flee repressive governments in the belief that they could live and speak freely. Now they find themselves questioning whether their adopted home is as safe as they once believed - or, perhaps, wanted to believe.
Their fear, they say, has been compounded by the British government’s muted response to their attacks and a lack of follow up from any UK law enforcement agency. What’s to stop them, the dissidents ask, from being targeted again, given that Citizen Lab now says that even Downing Street and the Foreign Office were infected with Pegasus, likely by the UAE?
Pegasus: How it hacks phones+ Show
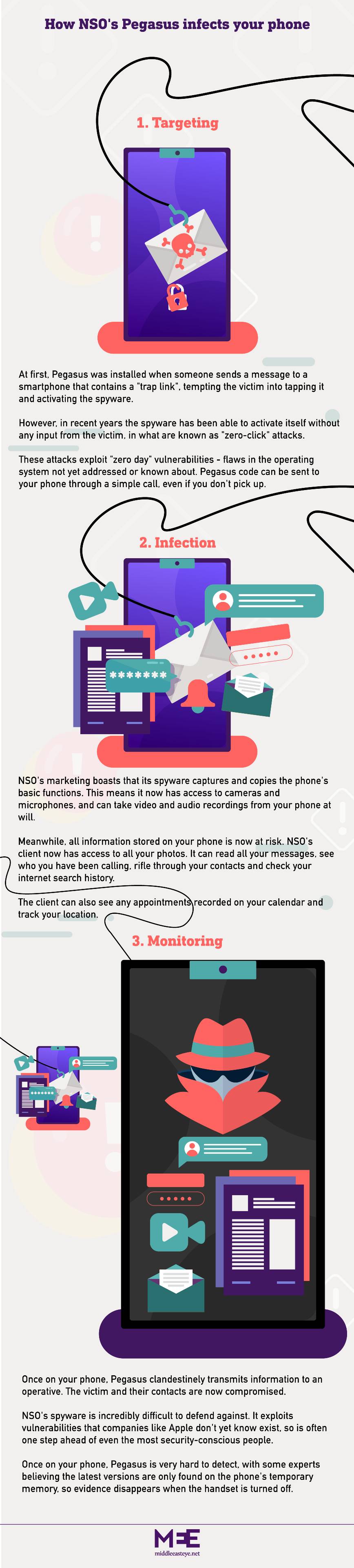
Like al-Masarir, all the dissidents MEE interviewed for this story had an inkling before they were hacked that the UK might not be fail-safe. One survived an early morning arson attempt on his family home. Another found a large knife outside his kitchen window the same day he received messages with knife emojis that read “Soon.”
Two others had their British bank accounts - and those of their family members - closed after the UAE designated the British-based organisations that they run and lead as terrorist organisations.
But the hacking, the dissidents say, has been disturbing in another way. There is something incredibly distressing, they say, about how their private lives were infiltrated in virtual space, and without their knowledge and with no other witnesses, in real time.
It’s an invisible, yet very real and potent trauma that digital rights expert Marwa Fatafta, MENA policy manager for Access Now, instantly recognises when I tell her the stories I’m hearing. “Surveillance is a form of violence,” she jumps in. “It violates your privacy, it violates your dignity, it violates your agency. You are always in a perpetual state of fear and anxiety, not only about yourself but also about others.”
The six men I spoke to have taken legal action in the UK against Bahrain, Saudi Arabia and the UAE, who are all accused of targeting them on separate occasions. Their hope is that British courts will act where they feel the British government and law enforcement has failed.
A judgement is imminent in the case al-Masarir has brought against Saudi Arabia over the spyware allegations as well as the August 2018 street attack. But it won’t be a final ruling: rather, the court will decide whether al-Masarir’s case for injuries and damages against the kingdom can proceed further. Usually a state would be shielded from most litigation in the UK, thanks to the State Immunity Act of 1978, enacted before spyware existed.
But al-Masarir’s lawyers at the UK law firm Leigh Day argue that what happened to him is an exception to that act. His case will be the first ruling from a UK court involving spyware and a foreign country, and could set precedent for other dissidents in the UK who have been targeted. It may also, say lawyers and surveillance experts, serve as inspiration for future litigation around the world.
MEE asked the Saudi, Emirati and Bahraini governments to comment on the legal action in the UK, but none replied.
Anas Altikriti, 53, is British-Iraqi. His father was a prominent opposition figure against the Ba’ath regime. The family left Iraq for the UK when Altikriti was a toddler. Spending much of his teenage years and his early 20s in the UAE where he attended school, Altikriti returned to the UK where he has campaigned against war and for democracy in the Middle East, run a foundation promoting dialogue between Islam and the West, and served as a hostage negotiator.
His typical poised, articulate self, Altikriti continues to speak fluently even as rain falls on us. But I’m struck that this is the first time in several interviews, over several years, that I’ve ever heard him discuss feelings when he explains what digital surveillance has done to him.
“It’s the unseen, the creeping up on you in your most safe and secure and sanctified place.”
Altikriti founded the Cordoba Foundation in 2005. It promotes dialogue between the West and Islam, as well as advising politicians on strategy and security in the Middle East. In 2014, it was designated as a terrorist organisation by the UAE - but the UK government said nothing, to the surprise of Altikriti. “At least clear your own name,” he said of the British government, “never mind me or Cordoba.”
 Anas Altikriti: "It’s the unseen, the creeping up on you in your most safe and secure and sanctified place." (MEE)
Anas Altikriti: "It’s the unseen, the creeping up on you in your most safe and secure and sanctified place." (MEE)
“That left a mark on my impression of how valuable or otherwise it was to be a British citizen. But this is probably the final nail in the coffin.”
Altikriti learned last summer that forensic investigators believe the UAE hacked his Iphone with Pegasus. Since then he has told people not to tell him their secrets, which is a bit tricky when you offer political advice to leaders and conduct hostage negotiations for a living.
His appetite for handling information that is even remotely off the record is now gone. “I say: ‘Look, I’d rather you didn’t [tell me something private] unless you have to because I don’t know if I’m the only one listening to this.”
Before the events of last summer, Altikriti’s phone was practically appended to his body, ready to be answered at any moment. Now he’s not sure when - or if - he wants it near him again. Those closest to him also feel the same. “I was with a group of friends and they laughed: ‘We need to be careful. Anas is carrying his phone’.” He shrugs.
“It’s deeply uncomfortable.”
Who hacked the phones?
Mohammed Kozbar, 56, is the chairman of Finsbury Park Mosque in north London. Two days after Ramadan has ended, we sit in the mosque’s emptied prayer hall which is quiet and soft underfoot as a breeze blows in from an open window. Kozbar too has an air of calmness, his tall frame gently perched on a folded chair. Yet he’s clearly uncomfortable speaking about himself.
He arrived in Britain in 1990 from Lebanon, which had been devastated by the drawn-out civil war. Since then he has focused on building the Muslim community in Britain: he is among those credited with turning the Finsbury Park Mosque around after it was dominated by Egyptian cleric Abu Hamza. As the mosque's iman, Hamza encouraged his followers to fight overseas, and was later convicted by a UK court for inciting violence before he was extradited to the US where he was found guilty of terrorism charges and jailed for life.
Kozbar regularly brings international law enforcement delegations to visit the mosque and observe how the they put Hamza's influence behind them.
Last July, Kozbar too discovered that his number was on the leaked list and had likely been targeted by the UAE. Citizen Lab analysed his phone and confirmed it had been infiltrated by Pegasus. He’s not sure why - only that he had previously spoken out against the UAE’s human rights record. Like Tikriti, he had had his British bank accounts shut down when the UAE named the Muslim Association of Britain, in which he and Altikriti have held leadership roles, as a terrorist entity.

Amid all this, Al-Masarir noticed something odd about his iPhones. Their batteries were dying quickly. They refused to update with the latest software. Puzzled, Al-Masarir contacted Citizen Lab, a group of academics at the University of Toronto who focus on communication technology, human rights and global security. It conducted a forensic investigation and discovered that the phones had been hacked with Pegasus, the spyware made by the Israeli company NSO Group that turns phones into military-grade surveillance devices.
Al-Masarir’s movements, his conversations, his photos and his messages, investigators found, had all been fed back to a Saudi server.
It’s now four years later. A cameraman and I are meeting with al-Masarir at a dot he’s marked on a map in this country park. These days, he tells me over an encrypted app, it’s better not to film at his house. I’ve watched clips of his show and an interview he gave to Channel 4 in January 2020, when he’s so chatty that the presenter is forced to cut him off. I’m half expecting Ghanem to jump out of a bush. Or climb out of the white van idling nearby.
But where is he?
Then a figure walks straight towards me. He introduces himself: it’s only then I realise that the man, wrapped in a thick scarf and heavy suede jacket on this hot June day, is the host of The Ghanem Show - or, at least, he was. Al-Masarir tells me, after we find a gnarly log to sit on, that he stopped filming after the events of 2018. “I couldn’t do my show, I couldn’t do anything,” he explains, carefully eyeballing in turn a dog walker, a family and two men passing by.
There had been earlier attempts to silence him. YouTube, says al-Masarir, shut down his channel twice at the request of the Saudi Broadcasting Agency. He had received death threats and threatening phone calls.
Under police protection, and scared to travel anywhere in central London, al-Masarir's life closed in on him. “It has affected me in my work life, my personal life, everything, that hacking," he says. "It has destroyed my appetite to do anything to be honest."
Pegasus in the UK
During the past year, story after story has emerged from nearly every continent of activists, journalists, politicians and others who have been the alleged targets of state-sponsored spyware attacks. Most relate to Pegasus and the leak of list containing more than 50,000 phone numbers. They include Middle East Eye staff.
But the sheer scale of the Pegasus Papers - which were just one leak, about one type of spyware - doesn’t begin to capture the impact that hacking has on the lives of its targets.
Among these are Arab dissidents who for decades have moved to the UK to flee repressive governments in the belief that they could live and speak freely. Now they find themselves questioning whether their adopted home is as safe as they once believed - or, perhaps, wanted to believe.
Their fear, they say, has been compounded by the British government’s muted response to their attacks and a lack of follow up from any UK law enforcement agency. What’s to stop them, the dissidents ask, from being targeted again, given that Citizen Lab now says that even Downing Street and the Foreign Office were infected with Pegasus, likely by the UAE?
Pegasus: How it hacks phones+ Show

Like al-Masarir, all the dissidents MEE interviewed for this story had an inkling before they were hacked that the UK might not be fail-safe. One survived an early morning arson attempt on his family home. Another found a large knife outside his kitchen window the same day he received messages with knife emojis that read “Soon.”
Two others had their British bank accounts - and those of their family members - closed after the UAE designated the British-based organisations that they run and lead as terrorist organisations.
But the hacking, the dissidents say, has been disturbing in another way. There is something incredibly distressing, they say, about how their private lives were infiltrated in virtual space, and without their knowledge and with no other witnesses, in real time.
It’s an invisible, yet very real and potent trauma that digital rights expert Marwa Fatafta, MENA policy manager for Access Now, instantly recognises when I tell her the stories I’m hearing. “Surveillance is a form of violence,” she jumps in. “It violates your privacy, it violates your dignity, it violates your agency. You are always in a perpetual state of fear and anxiety, not only about yourself but also about others.”
The six men I spoke to have taken legal action in the UK against Bahrain, Saudi Arabia and the UAE, who are all accused of targeting them on separate occasions. Their hope is that British courts will act where they feel the British government and law enforcement has failed.
A judgement is imminent in the case al-Masarir has brought against Saudi Arabia over the spyware allegations as well as the August 2018 street attack. But it won’t be a final ruling: rather, the court will decide whether al-Masarir’s case for injuries and damages against the kingdom can proceed further. Usually a state would be shielded from most litigation in the UK, thanks to the State Immunity Act of 1978, enacted before spyware existed.
But al-Masarir’s lawyers at the UK law firm Leigh Day argue that what happened to him is an exception to that act. His case will be the first ruling from a UK court involving spyware and a foreign country, and could set precedent for other dissidents in the UK who have been targeted. It may also, say lawyers and surveillance experts, serve as inspiration for future litigation around the world.
MEE asked the Saudi, Emirati and Bahraini governments to comment on the legal action in the UK, but none replied.
Anas Altikriti, 53, is British-Iraqi. His father was a prominent opposition figure against the Ba’ath regime. The family left Iraq for the UK when Altikriti was a toddler. Spending much of his teenage years and his early 20s in the UAE where he attended school, Altikriti returned to the UK where he has campaigned against war and for democracy in the Middle East, run a foundation promoting dialogue between Islam and the West, and served as a hostage negotiator.
His typical poised, articulate self, Altikriti continues to speak fluently even as rain falls on us. But I’m struck that this is the first time in several interviews, over several years, that I’ve ever heard him discuss feelings when he explains what digital surveillance has done to him.
“It’s the unseen, the creeping up on you in your most safe and secure and sanctified place.”
Altikriti founded the Cordoba Foundation in 2005. It promotes dialogue between the West and Islam, as well as advising politicians on strategy and security in the Middle East. In 2014, it was designated as a terrorist organisation by the UAE - but the UK government said nothing, to the surprise of Altikriti. “At least clear your own name,” he said of the British government, “never mind me or Cordoba.”
 Anas Altikriti: "It’s the unseen, the creeping up on you in your most safe and secure and sanctified place." (MEE)
Anas Altikriti: "It’s the unseen, the creeping up on you in your most safe and secure and sanctified place." (MEE)“That left a mark on my impression of how valuable or otherwise it was to be a British citizen. But this is probably the final nail in the coffin.”
Altikriti learned last summer that forensic investigators believe the UAE hacked his Iphone with Pegasus. Since then he has told people not to tell him their secrets, which is a bit tricky when you offer political advice to leaders and conduct hostage negotiations for a living.
His appetite for handling information that is even remotely off the record is now gone. “I say: ‘Look, I’d rather you didn’t [tell me something private] unless you have to because I don’t know if I’m the only one listening to this.”
Before the events of last summer, Altikriti’s phone was practically appended to his body, ready to be answered at any moment. Now he’s not sure when - or if - he wants it near him again. Those closest to him also feel the same. “I was with a group of friends and they laughed: ‘We need to be careful. Anas is carrying his phone’.” He shrugs.
“It’s deeply uncomfortable.”
Who hacked the phones?
Mohammed Kozbar, 56, is the chairman of Finsbury Park Mosque in north London. Two days after Ramadan has ended, we sit in the mosque’s emptied prayer hall which is quiet and soft underfoot as a breeze blows in from an open window. Kozbar too has an air of calmness, his tall frame gently perched on a folded chair. Yet he’s clearly uncomfortable speaking about himself.
He arrived in Britain in 1990 from Lebanon, which had been devastated by the drawn-out civil war. Since then he has focused on building the Muslim community in Britain: he is among those credited with turning the Finsbury Park Mosque around after it was dominated by Egyptian cleric Abu Hamza. As the mosque's iman, Hamza encouraged his followers to fight overseas, and was later convicted by a UK court for inciting violence before he was extradited to the US where he was found guilty of terrorism charges and jailed for life.
Kozbar regularly brings international law enforcement delegations to visit the mosque and observe how the they put Hamza's influence behind them.
Last July, Kozbar too discovered that his number was on the leaked list and had likely been targeted by the UAE. Citizen Lab analysed his phone and confirmed it had been infiltrated by Pegasus. He’s not sure why - only that he had previously spoken out against the UAE’s human rights record. Like Tikriti, he had had his British bank accounts shut down when the UAE named the Muslim Association of Britain, in which he and Altikriti have held leadership roles, as a terrorist entity.

Mohammed Kozbar: "I asked: ‘Are you 100 percent sure?' He confirmed: ‘Yes, I’m 100 percent sure.” (MEE)
Kozbar recalls the moment, while sat in the mosque, when a reporter told him what had happened to his phone. “I asked: ‘Are you 100 percent sure?' He confirmed: ‘Yes, I’m 100 percent sure.'”
Hours later, Kozbar explained to his wife and his children that photos and conversations they had shared hadn’t been private. And it is the thought of his family’s privacy being violated that has particularly disturbed him.
“What did you do, Baba?” his 13-year-old son asked. "I didn’t have an answer,” Kozbar says, his voice breaking. “I said: ‘I didn’t do anything.’” Kozbar now wonders where and if a file of his family’s messages and images may be sitting.
In contrast, Tikriti says he has no doubt that information collected when his phone was infected has already been used. At the time investigators say he was hacked, Tikriti was involved in four hostage negotiations, none of which involved the UAE.
One effort in particular, to secure the release of a young woman, had reached its final stages. But, Tikriti said, all communication stopped before the deal could be made and the hostage freed. He pauses. “I have negotiated probably 31 or 32 cases and never - never - has what I’ve just described to you happened.”
That was two years ago. To this day, Altikriti has no idea where or how the woman is - or what happened to the people in the region who tried to free her. “What kind of danger have they been put in as a result? Only God knows.”
Altikriti has struggled as to whether to tell the woman’s family that his phone was hacked. He feels burdened by the knowledge of how the deal went wrong - but decided that knowing the details wouldn’t benefit them. He coughs and seems uncharacteristically lost for words.
“The person who they were hanging a lot of hope on was not as secure as they were hoping. It’s nothing that I could have done. I didn’t realise it at the time. I didn’t realise it even after it went cold.”
It’s this not knowing that the lawyers involved in the legal action now underway say has been one of the harshest blows to their clients, and is fuelling their anxiety even now.
Monika Sobiecki, a partner at the UK law firm Bindmans which is representing Kozbar and Altikriti, says: “If it can be deployed against you once, then what’s the guarantee that it isn’t being deployed against you now?
“Effectively, what this creates is a panopticon - the world as a prison - and there is nowhere you can be safe from your persecutors because even if you’ve moved to what’s considered a safe, stable Western democracy, you can still be pursued and persecuted.”
Yahya Assiri is certainly not relaxed. “Honestly, I don’t feel safe in this country,” he tells me from the London office of ALQST, the human rights organisation he started in 2014 after he left his double life in Saudi Arabia.
On the surface, Assiri was a Saudi air force officer charged with weapons purchases. But he was also using the online pseudonym Abu Fares to raise concerns about issues including poverty, unemployment and repression. Eventually, he was going to be caught.
In 2014, he was studying human rights at Kingston University in south-west London when he heard from friends in Saudi Arabia that security forces were asking after him. It was then that Assiri realised that he could not return home.

Kozbar recalls the moment, while sat in the mosque, when a reporter told him what had happened to his phone. “I asked: ‘Are you 100 percent sure?' He confirmed: ‘Yes, I’m 100 percent sure.'”
Hours later, Kozbar explained to his wife and his children that photos and conversations they had shared hadn’t been private. And it is the thought of his family’s privacy being violated that has particularly disturbed him.
“What did you do, Baba?” his 13-year-old son asked. "I didn’t have an answer,” Kozbar says, his voice breaking. “I said: ‘I didn’t do anything.’” Kozbar now wonders where and if a file of his family’s messages and images may be sitting.
In contrast, Tikriti says he has no doubt that information collected when his phone was infected has already been used. At the time investigators say he was hacked, Tikriti was involved in four hostage negotiations, none of which involved the UAE.
One effort in particular, to secure the release of a young woman, had reached its final stages. But, Tikriti said, all communication stopped before the deal could be made and the hostage freed. He pauses. “I have negotiated probably 31 or 32 cases and never - never - has what I’ve just described to you happened.”
'If it can be deployed against you once, then what’s the guarantee that it isn’t being deployed against you now?'
- Monika Sobiecki, Bindmans lawyers
That was two years ago. To this day, Altikriti has no idea where or how the woman is - or what happened to the people in the region who tried to free her. “What kind of danger have they been put in as a result? Only God knows.”
Altikriti has struggled as to whether to tell the woman’s family that his phone was hacked. He feels burdened by the knowledge of how the deal went wrong - but decided that knowing the details wouldn’t benefit them. He coughs and seems uncharacteristically lost for words.
“The person who they were hanging a lot of hope on was not as secure as they were hoping. It’s nothing that I could have done. I didn’t realise it at the time. I didn’t realise it even after it went cold.”
It’s this not knowing that the lawyers involved in the legal action now underway say has been one of the harshest blows to their clients, and is fuelling their anxiety even now.
Monika Sobiecki, a partner at the UK law firm Bindmans which is representing Kozbar and Altikriti, says: “If it can be deployed against you once, then what’s the guarantee that it isn’t being deployed against you now?
“Effectively, what this creates is a panopticon - the world as a prison - and there is nowhere you can be safe from your persecutors because even if you’ve moved to what’s considered a safe, stable Western democracy, you can still be pursued and persecuted.”
Yahya Assiri is certainly not relaxed. “Honestly, I don’t feel safe in this country,” he tells me from the London office of ALQST, the human rights organisation he started in 2014 after he left his double life in Saudi Arabia.
On the surface, Assiri was a Saudi air force officer charged with weapons purchases. But he was also using the online pseudonym Abu Fares to raise concerns about issues including poverty, unemployment and repression. Eventually, he was going to be caught.
In 2014, he was studying human rights at Kingston University in south-west London when he heard from friends in Saudi Arabia that security forces were asking after him. It was then that Assiri realised that he could not return home.

Yahya Assiri: "The most painful thing is there were a large number of human rights advocates and dissidents targeted." (MEE)
For eight busy years now, Assiri has been criticising the kingdom’s policies and leaders from the UK. In addition to ALQST, he launched Diwan London, an online platform promoting freedom and justice in the Arab world. He also serves as the secretary-general of the National Assembly Party (NAAS), Saudi Arabia’s only opposition party, which is largely run by exiles.
But his work, particularly the networks he’s built, has made Assiri and his family a target. They have been threatened in public. They had their car broken into. It was outside their kitchen window that a knife was found.
Assiri himself is in the unenviable position, Citizen Lab investigators believe, of having been targeted by Pegasus not once, but twice. Both times, they suspect, were at the hands of Saudi Arabia. “The most painful thing is there were a large number of human rights advocates and dissidents targeted throughout this period, people I consider patriots, people working for the benefit of these countries."
In a pre-action letter sent in February to Khalid bin Bandar bin Sultan Al Saud, Saudi Arabia’s UK ambassador, Assiri’s lawyers say the amount of data that may have been exfiltrated from their client’s phone when it was infected “is nothing short of catastrophic” for their client and his contacts in the kingdom.
Those contacts include Loujain al-Hathloul, the prominent Saudi Arabian human rights activist who was among at least 10 Saudi Arabian women arrested in May 2018, weeks before the driving ban that they had long protested against was to be lifted. Al-Hathloul was held for 10 months and physically tortured before she was officially indicted. Her charge sheet is replete with references to her communications with “the renegade Yahya Assiri”.
Assiri says it’s hard to know for sure whether information from his phone or other devices was critical in the case of Hathloul or any of the other cases. Hathoul’s phones, too, have been hacked twice since 2017.
But Assiri suggests that to attempt to sort out which infiltration of what device led to which arrest is to miss the bigger picture. “It’s painful to know that the work we were doing was being spied on. But the most important thing isn’t necessarily that these authorities are trying to find out our secrets.
“It’s that they are trying to stop anyone speaking out against them or anyone challenging them.”
Bahraini dissidents tracked
Saeed Shehabi thought he had found the way to avoid being hacked. A veteran pro-democracy activist and journalist, as well as a leading figure in the Bahraini opposition movement, he is a trustee of the Abrar Islamic Foundation, a registered charity focused on Muslim education in the UK.
But when I call the foundation, the man on the other end of the phone apologises. Dr Shehabi is not in, he explains.
I ask if he can take a message to give to Shehabi.
“No, sorry,” he says. “He doesn’t have a mobile.”
When we eventually meet, Shehabi, 67, explains that he’s never had a phone. “I took precautions. I knew that I was targeted by our government because I have been a life-long opponent.” The not-having-a-phone strategy fits in with Shehabi’s old school, real-world methods.
Each Wednesday afternoon, he can be found protesting outside the Saudi embassy in London where he and others began demonstrating in March 2011 after the kingdom invaded Bahrain during pro-democracy protests. On Saturdays, he's at Downing Street, calling on the UK government to stop supporting Bahrain and training its security forces.
He is also, he tells me, an old hand when it comes to being surveilled. During the 1980s, he received at least three suspicious phone calls at his home in London from Bahrain that he believes were meant to catch him out.
One time, during a government crackdown, a fellow dissident called to arrange military training, despite Shehabi’s shock and insistence that this was not how the Bahraini opposition should operate. It later transpired that the friend was calling from a Bahraini prison. “They wanted to catch me with it,” Shehabi says of the call and others that followed. “The surveillance has always been there.”
In 2014, a leak revealed that Bahrain had allegedly hacked Shehabi’s computer using FinSpy surveillance software and potentially gained access to his email. The authorities could even control Shehabi’s laptop camera and microphones to watch and listen to him.
But Shehabi blamed himself.
“‘Are you so naive, Saeed?” he recalls he asked himself. “How can you allow your enemies to infiltrate you so easily?’" He turns back to me. “It’s not so easily. It has been paid for. It is an expensive procedure. But they managed to do it.”
Shehabi says the hacking revelation hit him especially hard because it came after his family escaped an early morning fire at their home in 2009. That in turn came two days after a pair of Bahraini dissidents were attacked in an alleyway near London’s Euston Station.
According to evidence Shehabi and other Bahrainis gave to the UK’s Foreign Affairs Committee in November 2012, they had been warned of “an imminent attack” before both incidents. After they were attacked on the street, the two dissidents say they were told by a caller that if they went near the Bahraini Embassy then “next time they would receive harsher punishment”.
It’s clear to Shehabi that these were attacks meant to silence them. “So when this [the hacking] happens, in light of these experiences, you say: ‘What is next?’”
Back in the woods on the outskirts of London, Ghanem al-Masirir seems more relaxed. During the past four years, he’s recounted the details of his life for dozens of journalists. He admits, once we are done filming, that it’s tiring.
“I’m getting older, and these years are just gone for nothing, and it’s a result of the Saudis,” he says. “I can’t get these years back, but hopefully I will stand up on my feet one day.”
Why don’t we have a coffee, he suggests. We’ve come a long way to see him and he wants to show us the neighbourhood where he lives. We pass by the white van and I tell him I thought he was going to jump out of it when we were looking for him earlier.
He pauses, and I worry I’ve said something wrong. Then he smiles and I see a familiar face. “Did you think I was being chopped up in there?” he laughs.
And we walk towards a busy suburb, Ghanem tucked between me and a cameraman, the sun momentarily on his face.
Illustration by Mohamed Elaasar / Hossam Sarhan, Middle East Eye
For eight busy years now, Assiri has been criticising the kingdom’s policies and leaders from the UK. In addition to ALQST, he launched Diwan London, an online platform promoting freedom and justice in the Arab world. He also serves as the secretary-general of the National Assembly Party (NAAS), Saudi Arabia’s only opposition party, which is largely run by exiles.
But his work, particularly the networks he’s built, has made Assiri and his family a target. They have been threatened in public. They had their car broken into. It was outside their kitchen window that a knife was found.
Assiri himself is in the unenviable position, Citizen Lab investigators believe, of having been targeted by Pegasus not once, but twice. Both times, they suspect, were at the hands of Saudi Arabia. “The most painful thing is there were a large number of human rights advocates and dissidents targeted throughout this period, people I consider patriots, people working for the benefit of these countries."
In a pre-action letter sent in February to Khalid bin Bandar bin Sultan Al Saud, Saudi Arabia’s UK ambassador, Assiri’s lawyers say the amount of data that may have been exfiltrated from their client’s phone when it was infected “is nothing short of catastrophic” for their client and his contacts in the kingdom.
Those contacts include Loujain al-Hathloul, the prominent Saudi Arabian human rights activist who was among at least 10 Saudi Arabian women arrested in May 2018, weeks before the driving ban that they had long protested against was to be lifted. Al-Hathloul was held for 10 months and physically tortured before she was officially indicted. Her charge sheet is replete with references to her communications with “the renegade Yahya Assiri”.
Assiri says it’s hard to know for sure whether information from his phone or other devices was critical in the case of Hathloul or any of the other cases. Hathoul’s phones, too, have been hacked twice since 2017.
But Assiri suggests that to attempt to sort out which infiltration of what device led to which arrest is to miss the bigger picture. “It’s painful to know that the work we were doing was being spied on. But the most important thing isn’t necessarily that these authorities are trying to find out our secrets.
“It’s that they are trying to stop anyone speaking out against them or anyone challenging them.”
Bahraini dissidents tracked
Saeed Shehabi thought he had found the way to avoid being hacked. A veteran pro-democracy activist and journalist, as well as a leading figure in the Bahraini opposition movement, he is a trustee of the Abrar Islamic Foundation, a registered charity focused on Muslim education in the UK.
But when I call the foundation, the man on the other end of the phone apologises. Dr Shehabi is not in, he explains.
I ask if he can take a message to give to Shehabi.
“No, sorry,” he says. “He doesn’t have a mobile.”
When we eventually meet, Shehabi, 67, explains that he’s never had a phone. “I took precautions. I knew that I was targeted by our government because I have been a life-long opponent.” The not-having-a-phone strategy fits in with Shehabi’s old school, real-world methods.
Each Wednesday afternoon, he can be found protesting outside the Saudi embassy in London where he and others began demonstrating in March 2011 after the kingdom invaded Bahrain during pro-democracy protests. On Saturdays, he's at Downing Street, calling on the UK government to stop supporting Bahrain and training its security forces.
'I’m getting older, and these years are just gone for nothing, and it’s a result of the Saudis'
- Ghanem al-Masirir
He is also, he tells me, an old hand when it comes to being surveilled. During the 1980s, he received at least three suspicious phone calls at his home in London from Bahrain that he believes were meant to catch him out.
One time, during a government crackdown, a fellow dissident called to arrange military training, despite Shehabi’s shock and insistence that this was not how the Bahraini opposition should operate. It later transpired that the friend was calling from a Bahraini prison. “They wanted to catch me with it,” Shehabi says of the call and others that followed. “The surveillance has always been there.”
In 2014, a leak revealed that Bahrain had allegedly hacked Shehabi’s computer using FinSpy surveillance software and potentially gained access to his email. The authorities could even control Shehabi’s laptop camera and microphones to watch and listen to him.
But Shehabi blamed himself.
“‘Are you so naive, Saeed?” he recalls he asked himself. “How can you allow your enemies to infiltrate you so easily?’" He turns back to me. “It’s not so easily. It has been paid for. It is an expensive procedure. But they managed to do it.”
Shehabi says the hacking revelation hit him especially hard because it came after his family escaped an early morning fire at their home in 2009. That in turn came two days after a pair of Bahraini dissidents were attacked in an alleyway near London’s Euston Station.
According to evidence Shehabi and other Bahrainis gave to the UK’s Foreign Affairs Committee in November 2012, they had been warned of “an imminent attack” before both incidents. After they were attacked on the street, the two dissidents say they were told by a caller that if they went near the Bahraini Embassy then “next time they would receive harsher punishment”.
It’s clear to Shehabi that these were attacks meant to silence them. “So when this [the hacking] happens, in light of these experiences, you say: ‘What is next?’”
Back in the woods on the outskirts of London, Ghanem al-Masirir seems more relaxed. During the past four years, he’s recounted the details of his life for dozens of journalists. He admits, once we are done filming, that it’s tiring.
“I’m getting older, and these years are just gone for nothing, and it’s a result of the Saudis,” he says. “I can’t get these years back, but hopefully I will stand up on my feet one day.”
Why don’t we have a coffee, he suggests. We’ve come a long way to see him and he wants to show us the neighbourhood where he lives. We pass by the white van and I tell him I thought he was going to jump out of it when we were looking for him earlier.
He pauses, and I worry I’ve said something wrong. Then he smiles and I see a familiar face. “Did you think I was being chopped up in there?” he laughs.
And we walk towards a busy suburb, Ghanem tucked between me and a cameraman, the sun momentarily on his face.
Illustration by Mohamed Elaasar / Hossam Sarhan, Middle East Eye
No comments:
Post a Comment