Spoofed AIS Signals Form Symbol of Russian Invasion
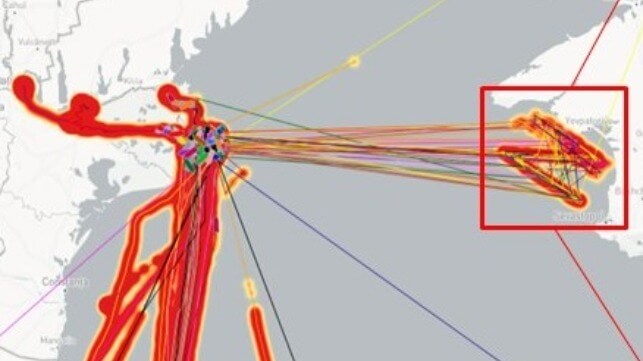
Geospatial intelligence firm Geollect has identified a spoofed AIS pattern tracing out the "Z" symbol of the Russian invasion of Ukraine at a position off the coast of Crimea. It is the latest in a long string of spoofing incidents in the region, and the pattern has long been attributed to Russian government actors.
Remote GPS spoofing can trick a GPS receiving unit into calculating a false location. Among other applications, this form of signal interference can be used to defeat the GPS guidance systems of certain U.S.- and NATO-made drones and precision weapons. Russia is reportedly proficient in this form of electronic warfare.
There is a long history of GPS spoofing incidents near Russian and Russian-occupied areas of the Black Sea coastline, and it periodically affects shipping. Since a ship's AIS transponder broadcasts the location it receives from a GPS unit, a broad-scale GPS spoofing attack will displace the "location" that the ship broadcasts via AIS, producing results that can sometimes appear bizarre. In 2017, more than 20 ships reported that their GPS positions had been erroneously relocated 25 nm inland to the airport in Novorossiysk. Others at anchor appeared "clustered" in areas where there were no radar returns for ships.
Over the course of 2017-19, non-profit analytics group C4ADS catalogued about 10,000 similar incidents affecting 1,300 vessels, most in or around areas of Russian influence. The report also drew a correlation between the movements of Russian President Vladimir Putin and the mass spoofing events, noted contributor and cybersecurity expert Dana Goward.
In June and July 2021, three NATO warships - the Royal Navy's USS Defender, the U.S. Navy's USS Ross and a Royal Dutch Navy vessel - all had their locations spoofed to positions off Russian-occupied Crimea. The reason and culprit remain unknown.
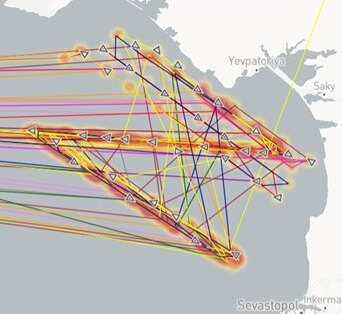 This month, a large number of merchant ships in and around the Bystry Canal region of Ukraine had their AIS locations remotely spoofed to the coastal waters of Russian-occupied Crimea. However, instead of a random pattern or a cluster, the AIS positions form a clear "Z" shape, the de facto symbol of support for the Russian invasion. (This precision AIS spoofing could also be performed in a simpler manner by transmitting false AIS signals, supplementing the ships' accurate AIS transmissions with corrupted duplicates.)
This month, a large number of merchant ships in and around the Bystry Canal region of Ukraine had their AIS locations remotely spoofed to the coastal waters of Russian-occupied Crimea. However, instead of a random pattern or a cluster, the AIS positions form a clear "Z" shape, the de facto symbol of support for the Russian invasion. (This precision AIS spoofing could also be performed in a simpler manner by transmitting false AIS signals, supplementing the ships' accurate AIS transmissions with corrupted duplicates.)
"It is highly likely that this is a deliberate information operation by a pro-Russian actor (possibly Russian military psychological operations) ahead of an anticipated Ukrainian counteroffensive and/or in celebration of Russia's proclaimed victory over Bakhmut," assessed Geollect.
The pattern began to show up on AIS on the 14th, and strengthened from May 19-21. Putin declared victory over Ukrainian forces in Bakhmut on May 22. In a clear sign of spoofing, merchant vessel "speeds" between these erroneous AIS positions were as high as 100 knots.
Chinese Hackers Target US Infrastructure Including Maritime Networks

The United States joined by its counterparts in the UK, Australia, Canada, and New Zealand, warned on Wednesday of “stealthy and targeted malicious activity,” focused on a broad range of computer networks including the maritime and transportation industries coming from a state-sponsored actor based in China. Microsoft said that it had detected the activity saying they believe it could disrupt critical communications infrastructure between the United States and the Asia region in the future.
The New York Times reports that the U.S. first became aware of the activity in February and has been working to analyze the extent of the incursion and damage done to systems. They are reporting that the attack focused on assets in Guam and the United States, highlighting the strategic role Guam plays for the U.S. military in its efforts in Asia, including the defense of Taiwan.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA), along with its partners in law enforcement and security, as well as Microsoft detailed the nature of the attack and steps that should be taken. They reported that it appears to be impacting organizations ranging from the communications, manufacturing, utility, transport, construction, maritime, government, information technology, and education sectors. Microsoft said it has notified targeted or compromised customers, but said the nature of the attack is both difficult to detect and mitigate because it infected valid accounts and uses a technique known as “living off the land.” Affected accounts will need to be closed or altered.
“For years, China has conducted aggressive cyber operations to steal intellectual property and sensitive data from organizations around the globe,” said Jen Easterly, CISA Director. “Today’s advisory highlights China’s continued use of sophisticated means to target our nation’s critical infrastructure, and it gives network defenders important insights into how to detect and mitigate this malicious activity.”
The attack is being carried out by a company known as Volt Typhoon, which Microsoft reports has been active since mid-2021. Microsoft explained that the attack works by trying to blend into normal network activity by routing traffic through compromised small office and home office network equipment. It seeks to collect data, archive the data, and maintain persistence, giving Microsoft “moderate confidence” that it is there to disrupt systems in the future.
News of this cybersecurity incident comes as the number of attacks from various sources increases on the maritime sector. The U.S. Coast Guard issued a separate alert yesterday warning of ongoing email phishing and malware intrusion attempts that targeted commercial vessels. It reported that cyber adversaries are attempting to gain sensitive information including the content of an official Notice of Arrival (NOA) using email addresses that pose as an official Port State Control authority. The Coast Guard has also received reports of malicious software designed to disrupt shipboard computer systems.
Various political factions in recent weeks have also raised concerns over the Chinese-manufactured cargo cranes used in most ports around the world. A legislative proposal has been introduced in the U.S. House of Representatives calling for a ban on Chinese-manufactured cranes and Chinese software despite a response from the American Association of Port Authorities highlighting that despite the “sensationalized claims” there is no evidence of the cranes being used to harm or track port operations.
The U.S. is not alone in being targeted. In January 2023, DNV’s ShipManager Service was attacked forcing the company to take the system offline for weeks. More than 7,000 vessels worldwide DNV reported were o the system with their access to the network suspended. It took till mid-March before the ships were brought back online with DNV reporting at the time that work to resume the full scope of service was still ongoing.
No comments:
Post a Comment