Tracking DarkSide Ransomware Gang's Profits
Elliptic Says It Traced Payments by Colonial Pipeline and Many Others
CRIMINAL CAPITALI$M = PRIMITIVE ACCUMULATION OF CAPITAL
Doug Olenick • May 18, 2021
Ransom payment amounts generated by DarkSide ransomware (Source: Elliptic)
The DarkSide ransomware gang apparently collected over $90 million in ransom payments from about 47 victims, including Colonial Pipeline Co., since the gang began operating in August 2020, according to the blockchain analytics firm Elliptic, which says it analyzed bitcoin wallet activity
Using the ransomware-as-a-service model, the DarkSide gang, which says it shut down operations as of May 13, provided malware to affiliates, who infect targeted computer systems and negotiate ransom payments. The DarkSide gang reportedly took a 25% share for ransoms less than $500,000, gradually decreasing to a 10% share for ransoms greater than $5 million, with the affiliates getting the remainder, writes Tom Robinson, Elliptic's co-founder and chief scientist, in a blog Tuesday.
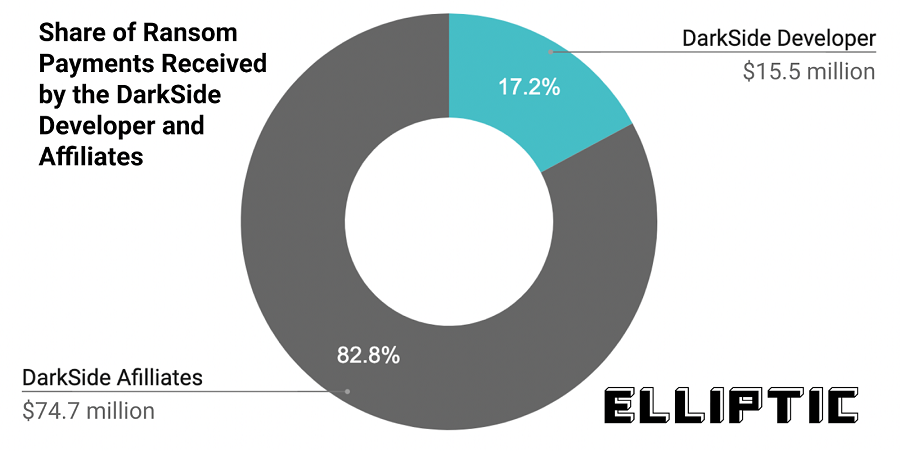
"This split of the ransom payment is very clear to see on the blockchain, with the different shares going to separate Bitcoin wallets controlled by the affiliate and developer," Robinson writes. "In total, the DarkSide developer has received bitcoins worth $15.5 million (17%), with the remaining $74.7 million (83%) going to the various affiliates."
The DarkSide ransomware gang apparently collected over $90 million in ransom payments from about 47 victims, including Colonial Pipeline Co., since the gang began operating in August 2020, according to the blockchain analytics firm Elliptic, which says it analyzed bitcoin wallet activity
Using the ransomware-as-a-service model, the DarkSide gang, which says it shut down operations as of May 13, provided malware to affiliates, who infect targeted computer systems and negotiate ransom payments. The DarkSide gang reportedly took a 25% share for ransoms less than $500,000, gradually decreasing to a 10% share for ransoms greater than $5 million, with the affiliates getting the remainder, writes Tom Robinson, Elliptic's co-founder and chief scientist, in a blog Tuesday.
"This split of the ransom payment is very clear to see on the blockchain, with the different shares going to separate Bitcoin wallets controlled by the affiliate and developer," Robinson writes. "In total, the DarkSide developer has received bitcoins worth $15.5 million (17%), with the remaining $74.7 million (83%) going to the various affiliates."
The DarkSide Operation
Elliptic says it identified 47 bitcoin wallets that made ransom payments to Darkside.
About 100 DarkSide attacks have been identified, so apparently almost 50% of the gang's attacks resulted in a ransom payment, with an average payment of $1.9 million, according to Elliptic's analysis.
Source: Elliptic
DarkSide's moneymaking empire started off slowly but peaked in February, when the group and its affiliates brought in just over $20 million, Elliptic says, based on its wallet research. Ransom payments totaled roughly $15 million in March, $8 million in April and $14 million in May, Elliptic reports.
Robinson says Elliptic, using proprietary blockchain analysis tools, tracked Colonial Pipeline paying DarkSide more than $5 million in two separate payments to a wallet on May 8 and May 10.
"May was set to be a record month, until DarkSide reportedly shut down its operations on May 13 and its bitcoin wallet was emptied," Robinson says.
In response to increased scrutiny from the cybersecurity industry and the federal government over the gang's attack on Colonial Pipeline Co., DarkSide announced it was abandoning its ransomware-as-a-service operation, issuing decryptor keys and making some financial restitution to its affiliates for lost business.
The cyber gang said it had lost contact with the infrastructure that enabled it to conduct ransomware operations and work with its affiliates (see: DarkSide Ransomware Gang Says It Has Shut Down).
On Tuesday, Brett Callow, threat analyst with Emsisoft, said DarkSide remained dark.
Colonial Pipeline's Payments
Elliptic says it determined that on May 8, 75 bitcoins, worth about $5 million at the time, were deposited by Colonial Pipeline into a DarkSide wallet, with another payment worth $320,000 added on May 10.
"Our analysis shows that the wallet has been active since 4th March 2021 and has received 57 payments from 21 different wallets. Some of these payments directly match ransoms known to have been paid to DarkSide by other victims, such as 78.29 BTC (worth $4.4 million) sent by chemical distribution company Brenntag on May 11," Robinson says.
Elliptic says it was able to zero in on the Colonial Pipeline payments because they originated from the currency exchange previously used by the pipeline company.
On May 9, the day after Colonial made its payment of 75 bitcoins, DarkSide removed a large portion of the bitcoin from its primary wallet, Elliptic says. The analytics company says that on May 13, the $5 million that remained in the wallet was removed by an unknown source.
"There has been speculation that the bitcoins were seized by the U.S. government," Robinson writes in a May 14 blog.
DarkSide's moneymaking empire started off slowly but peaked in February, when the group and its affiliates brought in just over $20 million, Elliptic says, based on its wallet research. Ransom payments totaled roughly $15 million in March, $8 million in April and $14 million in May, Elliptic reports.
Robinson says Elliptic, using proprietary blockchain analysis tools, tracked Colonial Pipeline paying DarkSide more than $5 million in two separate payments to a wallet on May 8 and May 10.
"May was set to be a record month, until DarkSide reportedly shut down its operations on May 13 and its bitcoin wallet was emptied," Robinson says.
In response to increased scrutiny from the cybersecurity industry and the federal government over the gang's attack on Colonial Pipeline Co., DarkSide announced it was abandoning its ransomware-as-a-service operation, issuing decryptor keys and making some financial restitution to its affiliates for lost business.
The cyber gang said it had lost contact with the infrastructure that enabled it to conduct ransomware operations and work with its affiliates (see: DarkSide Ransomware Gang Says It Has Shut Down).
On Tuesday, Brett Callow, threat analyst with Emsisoft, said DarkSide remained dark.
Colonial Pipeline's Payments
Elliptic says it determined that on May 8, 75 bitcoins, worth about $5 million at the time, were deposited by Colonial Pipeline into a DarkSide wallet, with another payment worth $320,000 added on May 10.
"Our analysis shows that the wallet has been active since 4th March 2021 and has received 57 payments from 21 different wallets. Some of these payments directly match ransoms known to have been paid to DarkSide by other victims, such as 78.29 BTC (worth $4.4 million) sent by chemical distribution company Brenntag on May 11," Robinson says.
Elliptic says it was able to zero in on the Colonial Pipeline payments because they originated from the currency exchange previously used by the pipeline company.
On May 9, the day after Colonial made its payment of 75 bitcoins, DarkSide removed a large portion of the bitcoin from its primary wallet, Elliptic says. The analytics company says that on May 13, the $5 million that remained in the wallet was removed by an unknown source.
"There has been speculation that the bitcoins were seized by the U.S. government," Robinson writes in a May 14 blog.
Money Laundering
"By tracing previous outflows from the wallet, we can gain insights into how DarkSide and its affiliates were laundering their previous proceeds," Robinson also writes. "What we find is that 18% of the bitcoin was sent to a small group of exchanges. This information will provide law enforcement with critical leads to identify the perpetrators of these attacks."
DarkSide sent another 4% of the money to a darknet money laundering marketplace named Hydra, which offers various criminal services, Elliptic says, based on its tracking.
"Hydra offers cash-out services alongside narcotics, hacking tools and fake IDs. These allow bitcoin to be converted into gift vouchers, prepaid debit cards, or cash rubles. If you're a Russian cybercriminal and you want to cash out your crypto, then Hydra is an attractive option," Robinson says.
Elliptic hopes that by identifying the bitcoin wallets used by DarkSide, fintech companies and crypto exchanges can be alerted to any client deposits that originate from a DarkSide wallet.
With this knowledge, "they can ensure that DarkSide and other ransomware operators cannot cash-out or exchange their bitcoin proceeds, disincentivizing this activity," Robinson says.
Dying Gasp Attack?
The day after DarkSide's May 13 declaration that it was shutting down, European subsidiaries of the Toshiba Tec Group confirmed they had been struck with a ransomware attack, Reuters reports. DarkSide was apparently responsible for this attack, based on research from the Japanese security firm Mitsui Bussan Secure Directions.
Toshiba says it immediately shut down communications between its European entities and Japan to stop the attack from spreading.
"As far as the investigation result shows, the group recognizes that it is possible that some information and data may have been leaked by the criminal gang. We will continue to conduct further investigation in cooperation with external specialized organization to grasp the details," the company said.
Toshiba has not released any additional information regarding the attack and has not responded to a request for additional information.
Data breach detection, prevention and notification - DataBreachToday
About the Author
Doug Olenick
News Editor, ISMG
Olenick has covered the cybersecurity and computer technology sectors for more than 25 years. Prior to joining ISMG as news editor, Olenick was online editor for SC Media, where he covered every aspect of the cybersecurity industry and managed the brand's online presence. Earlier, he worked at TWICE - This Week in Consumer Electronics - for 15 years. He also has contributed to Forbes.com, TheStreet and Mainstreet.
About the Author
Doug Olenick
News Editor, ISMG
Olenick has covered the cybersecurity and computer technology sectors for more than 25 years. Prior to joining ISMG as news editor, Olenick was online editor for SC Media, where he covered every aspect of the cybersecurity industry and managed the brand's online presence. Earlier, he worked at TWICE - This Week in Consumer Electronics - for 15 years. He also has contributed to Forbes.com, TheStreet and Mainstreet.
Marx's theory of primitive accumulation: a suggested ...
2005-08-05 · If any sense is to be made, therefore, of the notion of a 'primitive accumulation' (in Marx's sense of the term) prior in time to the full flowering of capitalist production, this must be interpreted in the first place as an accumulation of capital claims - - of titles to existing assets which are accumulated primarily for speculative reasons; and secondly as accumulation in the …
No comments:
Post a Comment