Erin Doherty, Jacob Knutson, Gigi Sukin

Illustration: Aïda Amer/Axios
A Russia-based hacking group known as REvil has compromised the computer systems of at least 1,000 businesses by targeting managed service providers, according to to the cybersecurity firm Huntress Labs Inc.
Why it matters: It's a large-scale ransomware campaign — the full scope of which is not yet known — and comes on the heels of several other high-profile ransomware attacks this year.
Of note via Bloomberg: "Such attacks can have a multiplying effect, since the hackers may then gain access and infiltrate the MSPs’ customers too."
The affected MSPs, platforms that provide IT management and other core network functions for businesses, and companies have not yet been named.
The latest: President Biden said Saturday that the U.S. government is still not certain who is behind the hack, according to Reuters.
"The initial thinking was it was not the Russian government but we're not sure yet," Biden said. Biden said he directed U.S. intelligences agencies to investigate.
Victims have emerged in 11 countries so far, per cybersecurity firm ESET.
Grocery chain Coop’s 800+ stores in Sweden couldn’t open Saturday after the hack led cash registers to malfunction, spokesperson Therese Knapp told Bloomberg.
What they're saying: John Hammond, a cybersecurity researcher at Huntress Labs, said more than 20 MSPs have been impacted. He noted the criminals targeted software supplier Kaseya, using its network-management package to spread the ransomware.
“What makes this attack stand out is the trickle-down effect, from the managed service provider to the small business,” Hammond said. “Kaseya handles large enterprise all the way to small businesses globally, so ultimately, it has the potential to spread to any size or scale business.”
Cybersecurity researcher Jake Williams, president of Rendition Infosec, told AP it's no accident that this happened before a holiday weekend, when IT staffing is generally thin.
Hackers frequently infiltrate widely used software, then spread malware as the software automatically updates.
The privately held Kaseya is based in Dublin, with a U.S. headquarters in Miami. The Miami Herald reported Kaseya's plans to hire as many as 500 workers by 2022 to staff a recently acquired cybersecurity platform.
The big picture: The breach comes after a summit between President Biden and Russian President Vladimir Putin, during which Biden threatened to use the U.S.' "significant" cyber capabilities to respond if critical infrastructure entities are targeted by Russian hackers.
FBI Director Christopher Wray told Congress in June that cyber threats against U.S. businesses are increasing "almost exponentially."
Go deeper: FBI: Russia-linked REvil behind ransomware attack on meatpacker JBS
Editor's note: This story will be updated as new information is released.
A cyber attack that immobilised US businesses ahead of the nation's July 4 holiday weekend will be investigated for links to Russia.
Key points:
US President Joe Biden says authorities are "not sure" whether Russia is behind the attack
Scores of businesses were affected by the attack, but estimates of how many vary
Cyber security experts say the attack is one of the largest of its kind
Security firm Huntress Labs suspects the so-called supply chain attack was carried out by a Russian gang called REvil, which has also been blamed for last month's attack on global meat packer JBS.
US President Joe Biden said authorities were "not certain" who was behind the attack, which experts say is one of the largest of its kind.
"The initial thinking was it was not the Russian government but we're not sure yet," he said.
Mr Biden said he had directed US intelligence agencies to investigate, and the United States would respond if it determined Russia was to blame.
The hackers who struck on Friday US time hijacked widely used technology management software from a supplier called Kaseya.
They changed a Kaseya tool used by companies that manage technology at smaller businesses. They then encrypted the files of those providers' customers.
Kaseya said on its own website on Friday that it was investigating a "potential attack".
It also said it had limited the attack to "a very small percentage of our customers … currently estimated at fewer than 40 worldwide".
But Huntress Labs said it was working with partners targeted in the attack, and the software was manipulated "to encrypt more than 1,000 companies".
"This is a colossal and devastating supply-chain attack," John Hammond from Huntress said.
Gerome Billois, a cybersecurity expert with Wavestone consultancy, said ransomware attacks typically only affected one business at a time.
"In this case, they attacked a company that provides software for managing data systems, allowing them to simultaneously target several dozen — possibly even hundreds — of companies," he said.
Supply chain attacks have crept to the top of the cybersecurity agenda in the wake of the United States accusing hackers of operating at the Russian government's direction and tampering with a network-monitoring tool built by Texas software firm SolarWinds.
While the attack appeared directed at the US, Swedish supermarket chain Coop revealed it had to close more than half of its stores due to outages linked to the attack.
The company said it lost control of its checkouts after a subcontractor was hacked.
ABC/wires
Plus: Cops seize 3D printers 'used to print guns', and more bits and bytes
IN BRIEF In what's looking like a nasty supply-chain attack, IT systems management biz Kaseya was compromised by miscreants, which then used its VSA product to infect its own customers and then their customers with ransomware.
At least 200 businesses were hit, according to infosec biz Huntress. Kaseya meanwhile initially estimated 40 worldwide were infected. It also told its clients to switch off their VSA data management and remote monitoring services immediately.
"We are experiencing a potential attack against the VSA that has been limited to a small number of on-premise customers only as of 1400 EDT today," it said in a Friday advisory.
"We are in the process of investigating the root cause of the incident with an abundance of caution but we recommend that you IMMEDIATELY shutdown your VSA server until you receive further notice from us. Its (sic) critical that you do this immediately, because one of the first things the attacker does is shut off administrative access to the VSA."
It appears that attackers got onto Kaseya's servers and included a copy of the REvil ransomware in a software update for customers that went out on Friday. It has also taken offline its software-as-a-service platform as a precaution.
"We have been advised by our outside experts that customers who experienced ransomware and receive a communication from the attackers should not click on any links – they may be weaponized," Kaseya's advisory added.
The Florida-based company told The Register it was working with the FBI. It's reported that among the victims is Sweden's grocery store chain Coop, a customer of one of Kaseya's customers, causing 500 stores to remain closed.
The Linkedin breach that wasn't
Earlier this week there were some reports that someone had put 700 million Linkedin records up for sale on the dark web. Rather than intrusion, LinkedIn said, someone who had scraped publicly available information, combined it with other available data, and was trying to make a buck or ten out of it.
"We want to be clear that this is not a data breach and no private LinkedIn member data was exposed," Linkedin said. "Our initial investigation has found that this data was scraped from LinkedIn and other various websites and includes the same data reported earlier this year in our April 2021 scraping update."
Scraping is a serious problem for Linkedin, one it has taken to the US Supreme Court over.
Western Digital devices caught in crossfire?
Last week, users of Western Digital's My Book Live found they had lost a lot of data after devices were remotely wiped via a security vulnerability.
At the time, the manufacturer said this was due to a malware attack. Having looked at the IP addresses and network traffic involved, security shop Censys suggested it looked likely that one criminal infected My Book kit and then a separate individual initiated the factory reset command, suggesting someone could be trying to take out a rival.
Western Digital, however, disagrees. "Our investigation shows that in some cases, the same attacker exploited both vulnerabilities on the device, as evidenced by the source IP," it said. "The first vulnerability was exploited to install a malicious binary on the device, and the second vulnerability was later exploited to reset the device."
In the meantime the firm is offering data recovery services to affected folks and promising My Book Live customers a trade-in service for My Cloud accounts.
Google tidies up Nest security
Google has announced that it's beefing up the security of devices in its smart home biz Nest, and made a five-year commitment to support existing products. This comes after it discontinued its Nest Secure home security system.
The Chocolate Factory said all devices sold since 2019 will adhere to the standards of the Internet of Secure Things Alliance (ioXt) on patching and security. In addition Google will publish the ioXt validation results for all of its kit so buyers can make an informed choice.
"A helpful home is a safe home, and Nest’s new safety center is part of making sure Nest products help take care of the people in your life and the world around you," Google said in a blog post.
US police seize 3D printers over gun charges
An unusual case of physical security came up this week after the Pennsylvania police took custody of two 3D printers that allegedly were used to manufacture parts for so-called ghost guns – unregulated firearms American cops and prosecutors aren't too keen on.
“Kenneth Wilson was caught manufacturing untrackable and untraceable firearms out of his home. Once assembled, these fully functional firearms often become a tool for senseless violence,” said the state's Attorney General Josh Shapiro.
“Ghost guns are quickly becoming the weapon of choice for criminals that take the lives of too many Pennsylvanians. My office is working overtime to target these gun traffickers and get illegal guns off our streets.”
In addition to the 3D printers, police also said they seized three ghost gun frames, three firearms, a small amount of methamphetamine, $1,140 in cash, and drug packaging equipment from the suspect's house. ®
July 2, 2021

A massive REvil ransomware attack affects multiple managed service providers and over a thousand of their customers through a reported Kaseya supply-chain attack.
Starting this afternoon, the REvil ransomware gang, aka Sodinokibi, targeted MSPs with thousands of customers, through what appears to be a Kaseya VSA supply-chain attack.
At this time, there eight known large MSPs that have been hit as part of this supply-chain attack.
Kaseya VSA is a cloud-based MSP platform that allows providers to perform patch management and client monitoring for their customers.
Huntress Labs' John Hammond has told BleepingComputer that all of the affected MSPs are using Kaseya VSA and that they have proof that their customers are being encrypted as well.
"We are tracking 20 MSPs where Kaseya VSA was used to encrypt over 1,000 business and are working in close collaboration with six of them," Hammond shared in blog post about the attack.
Kaseya issued a security advisory on their help desk site, warning all VSA customers to immediately shut down their VSA server to prevent the attack's spread while investigating.
"We are experiencing a potential attack against the VSA that has been limited to a small number of on-premise customers only as of 2:00 PM EDT today.
We are in the process of investigating the root cause of the incident with an abundance of caution but we recommend that you IMMEDIATELY shutdown your VSA server until you receive further notice from us.
Its critical that you do this immediately, because one of the first things the attacker does is shutoff administrative access to the VSA."
In a statement to BleepingComputer, Kaseya stated that they have shut down their SaaS servers and are working with other security firms to investigate the incident.
Most large-scale ransomware attacks are conducted late at night over the weekend when there is less staff to monitor the network.
As this attack happened midday on a Friday, the threat actors likely planned the time to coincide with the July 4th weekend in the USA, where it is common for staff to have a shorter workday before the holidays.
If you have first-hand information about this attack or information about affected companies, we would love to hear about it. You can confidentially contact us on Signal at +16469613731 or on Wire at @lawrenceabrams-bc.
REvil attack spread through auto-update
BleepingComputer has been told by both Huntress' John Hammond and Sophos' Mark Loman that the attacks on MSPs appear to be a supply chain attack through Kaseya VSA.
According to Hammond, Kaseya VSA will drop an agent.crt file to the c:\kworking folder, which is being distributed as an update called 'Kaseya VSA Agent Hot-fix.'
A PowerShell command is then launched that first disables various Microsoft Defender security features, such as real-time monitoring, Controlled Folder Access, script scanning, and network protection.
It will then decode the agent.crt file using the legitimate Windows certutil.exe command to extract an agent.exe file to the same folder, which is then launched to begin the encryption process.
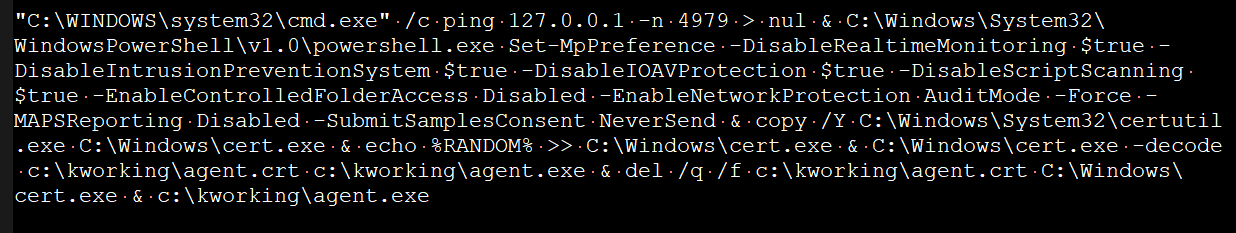 PowerShell command to execute the REvil ransomware
PowerShell command to execute the REvil ransomwareSource: Reddit
The agent.exe is signed using a certificate from "PB03 TRANSPORT LTD" and includes an embedded 'MsMpEng.exe' and 'mpsvc.dll,' with the DLL being the REvil encryptor. When extracted, the 'MsMpEng.exe' and 'mpsvc.dll' are placed in the C:\Windows folder.
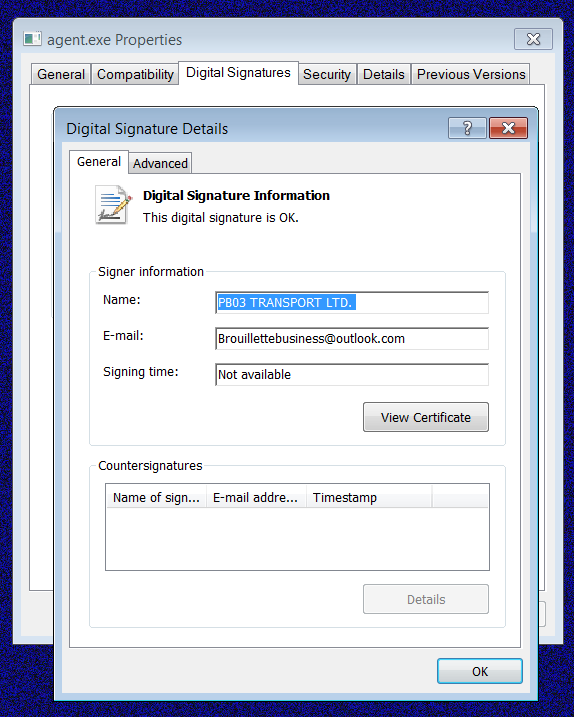
The MsMPEng.exe is an older version of the legitimate Microsoft Defender executable used as a LOLBin to launch the DLL and encrypt the device through a trusted executable.
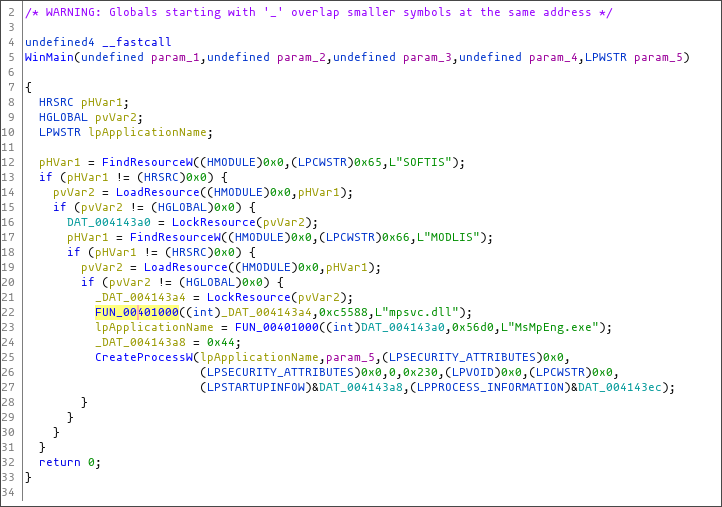
Some of the samples add politically charged Windows Registry keys and configurations changes to infected computers.
For example, a sample [VirusTotal] installed by BleepingComputer adds the HKLM\SOFTWARE\Wow6432Node\BlackLivesMatter key to store configuration information from the attack.
Advanced Intel's Vitali Kremez told BleepingComputer that another sample configures the device to launch REvil Safe Mode with a default password of 'DTrump4ever.'
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon]
"AutoAdminLogon"="1"
"DefaultUserName"="[account_name]"
"DefaultPassword"="DTrump4ever"
Kaseya CEO Fred Voccola told BleepingComputer in an email late Friday night that a vulnerability in Kaseya VSA was used during the attack and that a patch will be released as soon as possibly.
"While our investigation is ongoing, to date we believe that:
Our SaaS customers were never at-risk. We expect to restore service to those customers once we have confirmed that they are not at risk, which we expect will be within the next 24 hours;
Only a very small percentage of our customers were affected – currently estimated at fewer than 40 worldwide.
We believe that we have identified the source of the vulnerability and are preparing a patch to mitigate it for our on-premises customers that will be tested thoroughly. We will release that patch as quickly as possible to get our customers back up and running." - Kaseya.
BleepingComputer has sent followup questions regarding the vulnerability and was told a comprehensive update would be released Saturday afternoon.
Huntress continues to provide more info about the attack in a Reddit thread and we have added IOCs to the bottom of this article.
Ransomware gang demands a $5 million ransom
A sample of the REvil ransomware used in one of these attacks has been shared with BleepingComputer. However, it is unknown if this is the sample used for every victim or if each MSP received its own ransom demand.
The ransomware gang is demanding a $5,000,000 ransom to receive a decryptor from one of the samples.
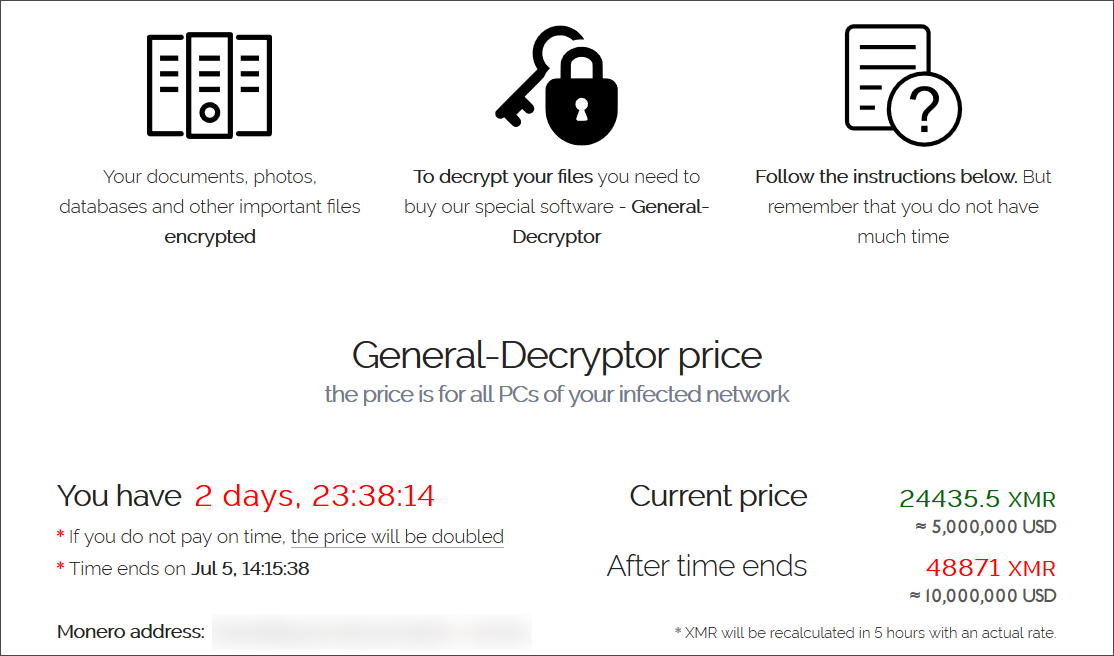
According to Emsisoft CTO Fabian Wosar, MSP customers who were affected by the attack received a much smaller $44,999 ransom demand.
While REvil is known to steal data before deploying the ransomware and encrypting devices, it is unknown if the attackers exfiltrated any files.
MSPs are a high-value target for ransomware gangs as they offer an easy channel to infecting many companies through a single breach, yet the attacks require intimate knowledge about MSPs and the software they use.
REvil has an affiliate well versed in the technology used by MSPs as they have a long history of targeting these companies and the software commonly used by them.
In June 2019, an REvil affiliate targeted MSPs via Remote Desktop and then used their management software to push ransomware installers to all of the endpoints that they manage.
This affiliate is believed to have previously worked with GandCrab, who also successfully conducted attacks against MSPs in January 2019.
This is a developing story and will continue to be updated.
Update 7/1/21 10:30 PM EST: Added updated statement about vulnerability.
Update 7/3/21 5:37 PM EST: Updated title and added information on how over 1,000 businesses have been affected this attack.




